Once you have deployed a Project Quay registry, there are many ways you can further configure and manage that deployment. Topics covered here include:
-
Advanced Project Quay configuration
-
Setting notifications to alert you of a new Project Quay release
-
Securing connections with SSL/TLS certificates
-
Directing action logs storage to Elasticsearch
-
Configuring image security scanning with Clair
-
Scan pod images with the Container Security Operator
-
Integrate Project Quay into OpenShift Container Platform with the Quay Bridge Operator
-
Mirroring images with repository mirroring
-
Sharing Project Quay images with a BitTorrent service
-
Authenticating users with LDAP
-
Enabling Quay for Prometheus and Grafana metrics
-
Setting up geo-replication
-
Troubleshooting Project Quay
For a complete list of Project Quay configuration fields, see the Configure Project Quay page.
Advanced Project Quay configuration
You can configure your Project Quay after initial deployment using one of the following methods:
-
Editing the
config.yamlfile. Theconfig.yamlfile contains most configuration information for the Project Quay cluster. Editing theconfig.yamlfile directly is the primary method for advanced tuning and enabling specific features. -
Using the Project Quay API. Some Project Quay features can be configured through the API.
This content in this section describes how to use each of the aforementioned interfaces and how to configure your deployment with advanced features.
Using the API to modify Project Quay
See the Project Quay API Guide for information on how to access Project Quay API.
Editing the config.yaml file to modify Project Quay
Advanced features can be implemented by editing the config.yaml file directly. All configuration fields for Project Quay features and settings are available in the Project Quay configuration guide.
The following example is one setting that you can change directly in the config.yaml file. Use this example as a reference when editing your config.yaml file for other features and settings.
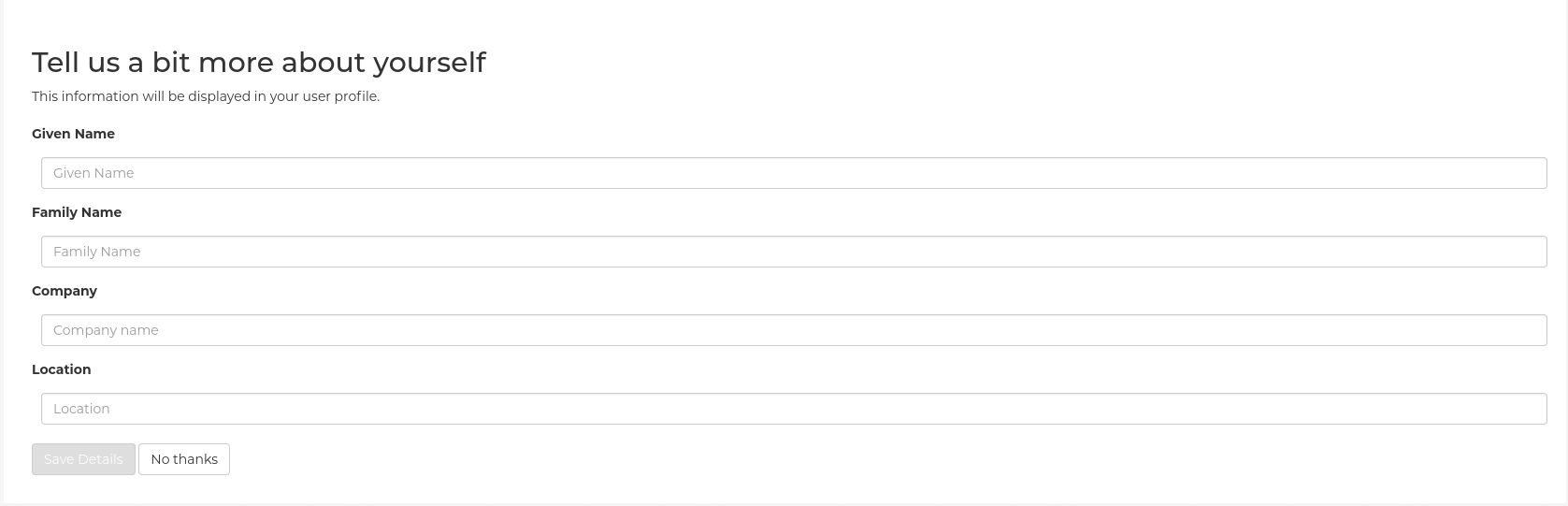
Adding name and company to Project Quay sign-in
By setting the FEATURE_USER_METADATA field to True, users are prompted for their name and company when they first sign in. This is an optional field, but can provide your with extra data about your Project Quay users.
Use the following procedure to add a name and a company to the Project Quay sign-in page.
-
Add, or set, the
FEATURE_USER_METADATAconfiguration field toTruein yourconfig.yamlfile. For example:
# ...
FEATURE_USER_METADATA: true
# ...-
Redeploy Project Quay.
-
Now, when prompted to log in, users are requested to enter the following information:
Using the configuration API
The configuration tool exposes 4 endpoints that can be used to build, validate, bundle and deploy a configuration. The config-tool API is documented at https://github.com/quay/config-tool/blob/master/pkg/lib/editor/API.md. In this section, you will see how to use the API to retrieve the current configuration and how to validate any changes you make.
Retrieving the default configuration
If you are running the configuration tool for the first time, and do not have an existing configuration, you can retrieve the default configuration. Start the container in config mode:
$ sudo podman run --rm -it --name quay_config \ -p 8080:8080 \ quay.io/projectquay/quay:v3.17.0 config secret
Use the config endpoint of the configuration API to get the default:
$ curl -X GET -u quayconfig:secret http://quay-server:8080/api/v1/config | jq
The value returned is the default configuration in JSON format:
{
"config.yaml": {
"AUTHENTICATION_TYPE": "Database",
"AVATAR_KIND": "local",
"DB_CONNECTION_ARGS": {
"autorollback": true,
"threadlocals": true
},
"DEFAULT_TAG_EXPIRATION": "2w",
"EXTERNAL_TLS_TERMINATION": false,
"FEATURE_ACTION_LOG_ROTATION": false,
"FEATURE_ANONYMOUS_ACCESS": true,
"FEATURE_APP_SPECIFIC_TOKENS": true,
....
}
}Retrieving the current configuration
If you have already configured and deployed the Quay registry, stop the container and restart it in configuration mode, loading the existing configuration as a volume:
$ sudo podman run --rm -it --name quay_config \ -p 8080:8080 \ -v $QUAY/config:/conf/stack:Z \ quay.io/projectquay/quay:v3.17.0 config secret
Use the config endpoint of the API to get the current configuration:
$ curl -X GET -u quayconfig:secret http://quay-server:8080/api/v1/config | jq
The value returned is the current configuration in JSON format, including database and Redis configuration data:
{
"config.yaml": {
....
"BROWSER_API_CALLS_XHR_ONLY": false,
"BUILDLOGS_REDIS": {
"host": "quay-server",
"password": "strongpassword",
"port": 6379
},
"DATABASE_SECRET_KEY": "4b1c5663-88c6-47ac-b4a8-bb594660f08b",
"DB_CONNECTION_ARGS": {
"autorollback": true,
"threadlocals": true
},
"DB_URI": "postgresql://quayuser:quaypass@quay-server:5432/quay",
"DEFAULT_TAG_EXPIRATION": "2w",
....
}
}Validating configuration using the API
You can validate a configuration by posting it to the config/validate endpoint:
curl -u quayconfig:secret --header 'Content-Type: application/json' --request POST --data '
{
"config.yaml": {
....
"BROWSER_API_CALLS_XHR_ONLY": false,
"BUILDLOGS_REDIS": {
"host": "quay-server",
"password": "strongpassword",
"port": 6379
},
"DATABASE_SECRET_KEY": "4b1c5663-88c6-47ac-b4a8-bb594660f08b",
"DB_CONNECTION_ARGS": {
"autorollback": true,
"threadlocals": true
},
"DB_URI": "postgresql://quayuser:quaypass@quay-server:5432/quay",
"DEFAULT_TAG_EXPIRATION": "2w",
....
}
} http://quay-server:8080/api/v1/config/validate | jq
The returned value is an array containing the errors found in the configuration. If the configuration is valid, an empty array [] is returned.
Determining the required fields
You can determine the required fields by posting an empty configuration structure to the config/validate endpoint:
curl -u quayconfig:secret --header 'Content-Type: application/json' --request POST --data '
{
"config.yaml": {
}
} http://quay-server:8080/api/v1/config/validate | jq
The value returned is an array indicating which fields are required:
[
{
"FieldGroup": "Database",
"Tags": [
"DB_URI"
],
"Message": "DB_URI is required."
},
{
"FieldGroup": "DistributedStorage",
"Tags": [
"DISTRIBUTED_STORAGE_CONFIG"
],
"Message": "DISTRIBUTED_STORAGE_CONFIG must contain at least one storage location."
},
{
"FieldGroup": "HostSettings",
"Tags": [
"SERVER_HOSTNAME"
],
"Message": "SERVER_HOSTNAME is required"
},
{
"FieldGroup": "HostSettings",
"Tags": [
"SERVER_HOSTNAME"
],
"Message": "SERVER_HOSTNAME must be of type Hostname"
},
{
"FieldGroup": "Redis",
"Tags": [
"BUILDLOGS_REDIS"
],
"Message": "BUILDLOGS_REDIS is required"
}
]Getting Project Quay release notifications
To keep up with the latest Project Quay releases and other changes related to Project Quay, you can sign up for update notifications on the Red Hat Customer Portal. After signing up for notifications, you will receive notifications letting you know when there is new a Project Quay version, updated documentation, or other Project Quay news.
-
Log into the Red Hat Customer Portal with your Red Hat customer account credentials.
-
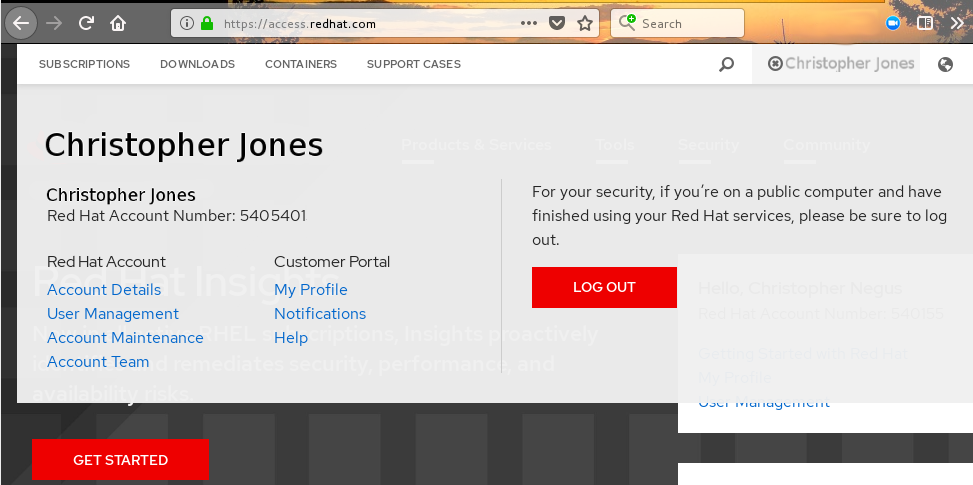
Select your user name (upper-right corner) to see Red Hat Account and Customer Portal selections:
-
Select Notifications. Your profile activity page appears.
-
Select the Notifications tab.
-
Select Manage Notifications.
-
Select Follow, then choose Products from the drop-down box.
-
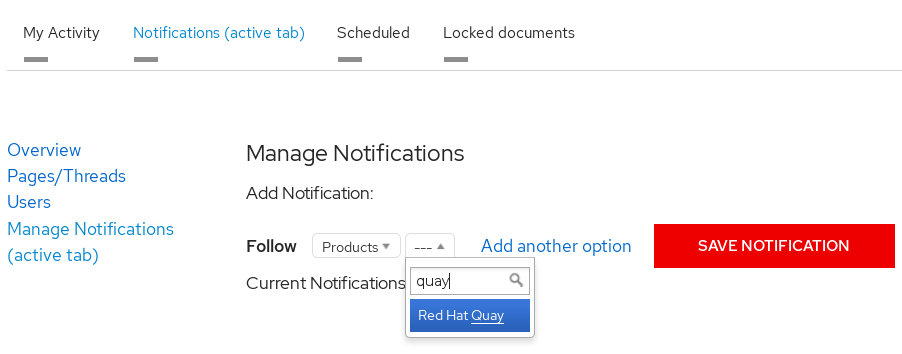
From the drop-down box next to the Products, search for and select Project Quay:
-
Select the SAVE NOTIFICATION button. Going forward, you will receive notifications when there are changes to the Project Quay product, such as a new release.
Using SSL to protect connections to Project Quay
Using SSL/TLS
Documentation for Using SSL/TLS has been revised and moved to Securing Project Quay. This chapter will be removed in a future version of Project Quay.
Configuring action log storage for Elasticsearch and Splunk
By default, usage logs are stored in the Project Quay database and exposed through the web UI on organization and repository levels. Appropriate administrative privileges are required to see log entries. For deployments with a large amount of logged operations, you can store the usage logs in Elasticsearch and Splunk instead of the Project Quay database backend.
Configuring action log storage for Elasticsearch
|
Note
|
To configure action log storage for Elasticsearch, you must provide your own Elasticsearch stack; it is not included with Project Quay as a customizable component. |
Enabling Elasticsearch logging can be done during Project Quay deployment or post-deployment by updating your config.yaml file. When configured, usage log access continues to be provided through the web UI for repositories and organizations.
Use the following procedure to configure action log storage for Elasticsearch:
-
Obtain an Elasticsearch account.
-
Update your Project Quay
config.yamlfile to include the following information:# ... LOGS_MODEL: elasticsearch (1) LOGS_MODEL_CONFIG: producer: elasticsearch (2) elasticsearch_config: host: http://<host.elasticsearch.example>:<port> (3) port: 9200 (4) access_key: <access_key> (5) secret_key: <secret_key> (6) use_ssl: True (7) index_prefix: <logentry> (8) aws_region: <us-east-1> (9) # ...-
The method for handling log data.
-
Choose either Elasticsearch or Kinesis to direct logs to an intermediate Kinesis stream on AWS. You need to set up your own pipeline to send logs from Kinesis to Elasticsearch, for example, Logstash.
-
The hostname or IP address of the system providing the Elasticsearch service.
-
The port number providing the Elasticsearch service on the host you just entered. Note that the port must be accessible from all systems running the Project Quay registry. The default is TCP port
9200. -
The access key needed to gain access to the Elasticsearch service, if required.
-
The secret key needed to gain access to the Elasticsearch service, if required.
-
Whether to use SSL/TLS for Elasticsearch. Defaults to
True. -
Choose a prefix to attach to log entries.
-
If you are running on AWS, set the AWS region (otherwise, leave it blank).
-
-
Optional. If you are using Kinesis as your logs producer, you must include the following fields in your
config.yamlfile:kinesis_stream_config: stream_name: <kinesis_stream_name> (1) access_key: <aws_access_key> (2) secret_key: <aws_secret_key> (3) aws_region: <aws_region> (4)-
The name of the Kinesis stream.
-
The name of the AWS access key needed to gain access to the Kinesis stream, if required.
-
The name of the AWS secret key needed to gain access to the Kinesis stream, if required.
-
The Amazon Web Services (AWS) region.
-
-
Save your
config.yamlfile and restart your Project Quay deployment.
Configuring action log storage for Splunk
Splunk is an alternative to Elasticsearch that can provide log analyses for your Project Quay data.
Enabling Splunk logging can be done during Project Quay deployment or post-deployment using the configuration tool. Configuration includes both the option to forward action logs directly to Splunk or to the Splunk HTTP Event Collector (HEC).
Use the following procedures to enable Splunk for your Project Quay deployment.
Installing and creating a username for Splunk
Use the following procedure to install and create Splunk credentials.
-
Create a Splunk account by navigating to Splunk and entering the required credentials.
-
Navigate to the Splunk Enterprise Free Trial page, select your platform and installation package, and then click Download Now.
-
Install the Splunk software on your machine. When prompted, create a username, for example,
splunk_adminand password. -
After creating a username and password, a localhost URL will be provided for your Splunk deployment, for example,
http://<sample_url>.remote.csb:8000/. Open the URL in your preferred browser. -
Log in with the username and password you created during installation. You are directed to the Splunk UI.
Generating a Splunk token
Use one of the following procedures to create a bearer token for Splunk.
Generating a Splunk token using the Splunk UI
Use the following procedure to create a bearer token for Splunk using the Splunk UI.
-
You have installed Splunk and created a username.
-
On the Splunk UI, navigate to Settings → Tokens.
-
Click Enable Token Authentication.
-
Ensure that Token Authentication is enabled by clicking Token Settings and selecting Token Authentication if necessary.
-
Optional: Set the expiration time for your token. This defaults at 30 days.
-
Click Save.
-
Click New Token.
-
Enter information for User and Audience.
-
Optional: Set the Expiration and Not Before information.
-
Click Create. Your token appears in the Token box. Copy the token immediately.
ImportantIf you close out of the box before copying the token, you must create a new token. The token in its entirety is not available after closing the New Token window.
Generating a Splunk token using the CLI
Use the following procedure to create a bearer token for Splunk using the CLI.
-
You have installed Splunk and created a username.
-
In your CLI, enter the following
CURLcommand to enable token authentication, passing in your Splunk username and password:$ curl -k -u <username>:<password> -X POST <scheme>://<host>:<port>/services/admin/token-auth/tokens_auth -d disabled=false -
Create a token by entering the following
CURLcommand, passing in your Splunk username and password.$ curl -k -u <username>:<password> -X POST <scheme>://<host>:<port>/services/authorization/tokens?output_mode=json --data name=<username> --data audience=Users --data-urlencode expires_on=+30d -
Save the generated bearer token.
Configuring Project Quay to use Splunk
Use the following procedure to configure Project Quay to use Splunk or the Splunk HTTP Event Collector (HEC).
-
You have installed Splunk and created a username.
-
You have generated a Splunk bearer token.
-
Configure Project Quay to use Splunk or the Splunk HTTP Event Collector (HEC).
-
If opting to use Splunk, open your Project Quay
config.yamlfile and add the following configuration fields:# ... LOGS_MODEL: splunk LOGS_MODEL_CONFIG: producer: splunk splunk_config: host: http://<user_name>.remote.csb (1) port: 8089 (2) bearer_token: <bearer_token> (3) url_scheme: <http/https> (4) verify_ssl: False (5) index_prefix: <splunk_log_index_name> (6) ssl_ca_path: <location_to_ssl-ca-cert.pem> (7) # ...-
String. The Splunk cluster endpoint.
-
Integer. The Splunk management cluster endpoint port. Differs from the Splunk GUI hosted port. Can be found on the Splunk UI under Settings → Server Settings → General Settings.
-
String. The generated bearer token for Splunk.
-
String. The URL scheme for access the Splunk service. If Splunk is configured to use TLS/SSL, this must be
https. -
Boolean. Whether to enable TLS/SSL. Defaults to
True. -
String. The Splunk index prefix. Can be a new, or used, index. Can be created from the Splunk UI.
-
String. The relative container path to a single
.pemfile containing a certificate authority (CA) for TLS/SSL validation.
-
-
If opting to use Splunk HEC, open your Project Quay
config.yamlfile and add the following configuration fields:# ... LOGS_MODEL: splunk LOGS_MODEL_CONFIG: producer: splunk_hec (1) splunk_hec_config: (2) host: prd-p-aaaaaq.splunkcloud.com (3) port: 8088 (4) hec_token: 12345678-1234-1234-1234-1234567890ab (5) url_scheme: https (6) verify_ssl: False (7) index: quay (8) splunk_host: quay-dev (9) splunk_sourcetype: quay_logs (10) timeout: 10 (11) # ...-
Specify
splunk_hecwhen configuring Splunk HEC. -
Logs model configuration for Splunk HTTP event collector action logs configuration.
-
The Splunk cluster endpoint.
-
Splunk management cluster endpoint port.
-
HEC token for Splunk.
-
The URL scheme for access the Splunk service. If Splunk is behind SSL/TLS, must be
https. -
Boolean. Enable (true) or disable (false) SSL/TLS verification for HTTPS connections.
-
The Splunk index to use.
-
The host name to log this event.
-
The name of the Splunk
sourcetypeto use. -
Timeout in seconds for HTTP requests to Splunk HEC endpoint. Prevents requests from hanging indefinitely when Splunk is unresponsive.
-
-
-
If you are configuring
ssl_ca_path, you must configure the SSL/TLS certificate so that Project Quay will trust it.-
If you are using a standalone deployment of Project Quay, SSL/TLS certificates can be provided by placing the certificate file inside of the
extra_ca_certsdirectory, or inside of the relative container path and specified byssl_ca_path. -
If you are using the Project Quay Operator, create a config bundle secret, including the certificate authority (CA) of the Splunk server. For example:
$ oc create secret generic --from-file config.yaml=./config_390.yaml --from-file extra_ca_cert_splunkserver.crt=./splunkserver.crt config-bundle-secretSpecify the
conf/stack/extra_ca_certs/splunkserver.crtfile in yourconfig.yaml. For example:# ... LOGS_MODEL: splunk LOGS_MODEL_CONFIG: producer: splunk splunk_config: host: ec2-12-345-67-891.us-east-2.compute.amazonaws.com port: 8089 bearer_token: eyJra url_scheme: https verify_ssl: true index_prefix: quay123456 ssl_ca_path: conf/stack/splunkserver.crt # ...
-
Creating an action log
Use the following procedure to create a user account that can forward action logs to Splunk.
|
Important
|
You must use the Splunk UI to view Project Quay action logs. At this time, viewing Splunk action logs on the Project Quay Usage Logs page is unsupported, and returns the following message: |
-
You have installed Splunk and created a username.
-
You have generated a Splunk bearer token.
-
You have configured your Project Quay
config.yamlfile to enable Splunk.
-
Log in to your Project Quay deployment.
-
Click on the name of the organization that you will use to create an action log for Splunk.
-
In the navigation pane, click Robot Accounts → Create Robot Account.
-
When prompted, enter a name for the robot account, for example
spunkrobotaccount, then click Create robot account. -
On your browser, open the Splunk UI.
-
Click Search and Reporting.
-
In the search bar, enter the name of your index, for example,
<splunk_log_index_name>and press Enter.The search results populate on the Splunk UI. Logs are forwarded in JSON format. A response might look similar to the following:
{ "log_data": { "kind": "authentication", (1) "account": "quayuser123", (2) "performer": "John Doe", (3) "repository": "projectQuay", (4) "ip": "192.168.1.100", (5) "metadata_json": {...}, (6) "datetime": "2024-02-06T12:30:45Z" (7) } }-
Specifies the type of log event. In this example,
authenticationindicates that the log entry relates to an authentication event. -
The user account involved in the event.
-
The individual who performed the action.
-
The repository associated with the event.
-
The IP address from which the action was performed.
-
Might contain additional metadata related to the event.
-
The timestamp of when the event occurred.
-
Understanding usage logs
By default, usage logs are stored in the Project Quay database. They are exposed through the web UI, on the organization and repository levels, and in the Superuser Admin Panel.
Database logs capture a wide ranges of events in Project Quay, such as the changing of account plans, user actions, and general operations. Log entries include information such as the action performed (kind_id), the user who performed the action (account_id or performer_id), the timestamp (datetime), and other relevant data associated with the action (metadata_json).
Viewing database logs
The following procedure shows you how to view repository logs that are stored in a PostgreSQL database.
-
You have administrative privileges.
-
You have installed the
psqlCLI tool.
-
Enter the following command to log in to your Project Quay PostgreSQL database:
$ psql -h <quay-server.example.com> -p 5432 -U <user_name> -d <database_name>Example outputpsql (16.1, server 13.7) Type "help" for help. -
Optional. Enter the following command to display the tables list of your PostgreSQL database:
quay=> \dtExample outputList of relations Schema | Name | Type | Owner --------+----------------------------+-------+---------- public | logentry | table | quayuser public | logentry2 | table | quayuser public | logentry3 | table | quayuser public | logentrykind | table | quayuser ... -
You can enter the following command to return a list of
repository_idsthat are required to return log information:quay=> SELECT id, name FROM repository;Example outputid | name ----+--------------------- 3 | new_repository_name 6 | api-repo 7 | busybox ... -
Enter the following command to use the
logentry3relation to show log information about one of your repositories:SELECT * FROM logentry3 WHERE repository_id = <repository_id>;Example outputid | kind_id | account_id | performer_id | repository_id | datetime | ip | metadata_json 59 | 14 | 2 | 1 | 6 | 2024-05-13 15:51:01.897189 | 192.168.1.130 | {"repo": "api-repo", "namespace": "test-org"}In the above example, the following information is returned:
{ "log_data": { "id": 59 (1) "kind_id": "14", (2) "account_id": "2", (3) "performer_id": "1", (4) "repository_id": "6", (5) "ip": "192.168.1.100", (6) "metadata_json": {"repo": "api-repo", "namespace": "test-org"} (7) "datetime": "2024-05-13 15:51:01.897189" (8) } }-
The unique identifier for the log entry.
-
The action that was done. In this example, it was
14. The key, or table, in the following section shows you that thiskind_idis related to the creation of a repository. -
The account that performed the action.
-
The performer of the action.
-
The repository that the action was done on. In this example,
6correlates to theapi-repothat was discovered in Step 3. -
The IP address where the action was performed.
-
Metadata information, including the name of the repository and its namespace.
-
The time when the action was performed.
-
Log entry kind_ids
The following table represents the kind_ids associated with Project Quay actions.
| kind_id | Action | Description |
|---|---|---|
1 |
account_change_cc |
Change of credit card information. |
2 |
account_change_password |
Change of account password. |
3 |
account_change_plan |
Change of account plan. |
4 |
account_convert |
Account conversion. |
5 |
add_repo_accesstoken |
Adding an access token to a repository. |
6 |
add_repo_notification |
Adding a notification to a repository. |
7 |
add_repo_permission |
Adding permissions to a repository. |
8 |
add_repo_webhook |
Adding a webhook to a repository. |
9 |
build_dockerfile |
Building a Dockerfile. |
10 |
change_repo_permission |
Changing permissions of a repository. |
11 |
change_repo_visibility |
Changing the visibility of a repository. |
12 |
create_application |
Creating an application. |
13 |
create_prototype_permission |
Creating permissions for a prototype. |
14 |
create_repo |
Creating a repository. |
15 |
create_robot |
Creating a robot (service account or bot). |
16 |
create_tag |
Creating a tag. |
17 |
delete_application |
Deleting an application. |
18 |
delete_prototype_permission |
Deleting permissions for a prototype. |
19 |
delete_repo |
Deleting a repository. |
20 |
delete_repo_accesstoken |
Deleting an access token from a repository. |
21 |
delete_repo_notification |
Deleting a notification from a repository. |
22 |
delete_repo_permission |
Deleting permissions from a repository. |
23 |
delete_repo_trigger |
Deleting a repository trigger. |
24 |
delete_repo_webhook |
Deleting a webhook from a repository. |
25 |
delete_robot |
Deleting a robot. |
26 |
delete_tag |
Deleting a tag. |
27 |
manifest_label_add |
Adding a label to a manifest. |
28 |
manifest_label_delete |
Deleting a label from a manifest. |
29 |
modify_prototype_permission |
Modifying permissions for a prototype. |
30 |
move_tag |
Moving a tag. |
31 |
org_add_team_member |
Adding a member to a team. |
32 |
org_create_team |
Creating a team within an organization. |
33 |
org_delete_team |
Deleting a team within an organization. |
34 |
org_delete_team_member_invite |
Deleting a team member invitation. |
35 |
org_invite_team_member |
Inviting a member to a team in an organization. |
36 |
org_remove_team_member |
Removing a member from a team. |
37 |
org_set_team_description |
Setting the description of a team. |
38 |
org_set_team_role |
Setting the role of a team. |
39 |
org_team_member_invite_accepted |
Acceptance of a team member invitation. |
40 |
org_team_member_invite_declined |
Declining of a team member invitation. |
41 |
pull_repo |
Pull from a repository. |
42 |
push_repo |
Push to a repository. |
43 |
regenerate_robot_token |
Regenerating a robot token. |
44 |
repo_verb |
Generic repository action (specifics might be defined elsewhere). |
45 |
reset_application_client_secret |
Resetting the client secret of an application. |
46 |
revert_tag |
Reverting a tag. |
47 |
service_key_approve |
Approving a service key. |
48 |
service_key_create |
Creating a service key. |
49 |
service_key_delete |
Deleting a service key. |
50 |
service_key_extend |
Extending a service key. |
51 |
service_key_modify |
Modifying a service key. |
52 |
service_key_rotate |
Rotating a service key. |
53 |
setup_repo_trigger |
Setting up a repository trigger. |
54 |
set_repo_description |
Setting the description of a repository. |
55 |
take_ownership |
Taking ownership of a resource. |
56 |
update_application |
Updating an application. |
57 |
change_repo_trust |
Changing the trust level of a repository. |
58 |
reset_repo_notification |
Resetting repository notifications. |
59 |
change_tag_expiration |
Changing the expiration date of a tag. |
60 |
create_app_specific_token |
Creating an application-specific token. |
61 |
revoke_app_specific_token |
Revoking an application-specific token. |
62 |
toggle_repo_trigger |
Toggling a repository trigger on or off. |
63 |
repo_mirror_enabled |
Enabling repository mirroring. |
64 |
repo_mirror_disabled |
Disabling repository mirroring. |
65 |
repo_mirror_config_changed |
Changing the configuration of repository mirroring. |
66 |
repo_mirror_sync_started |
Starting a repository mirror sync. |
67 |
repo_mirror_sync_failed |
Repository mirror sync failed. |
68 |
repo_mirror_sync_success |
Repository mirror sync succeeded. |
69 |
repo_mirror_sync_now_requested |
Immediate repository mirror sync requested. |
70 |
repo_mirror_sync_tag_success |
Repository mirror tag sync succeeded. |
71 |
repo_mirror_sync_tag_failed |
Repository mirror tag sync failed. |
72 |
repo_mirror_sync_test_success |
Repository mirror sync test succeeded. |
73 |
repo_mirror_sync_test_failed |
Repository mirror sync test failed. |
74 |
repo_mirror_sync_test_started |
Repository mirror sync test started. |
75 |
change_repo_state |
Changing the state of a repository. |
76 |
create_proxy_cache_config |
Creating proxy cache configuration. |
77 |
delete_proxy_cache_config |
Deleting proxy cache configuration. |
78 |
start_build_trigger |
Starting a build trigger. |
79 |
cancel_build |
Cancelling a build. |
80 |
org_create |
Creating an organization. |
81 |
org_delete |
Deleting an organization. |
82 |
org_change_email |
Changing organization email. |
83 |
org_change_invoicing |
Changing organization invoicing. |
84 |
org_change_tag_expiration |
Changing organization tag expiration. |
85 |
org_change_name |
Changing organization name. |
86 |
user_create |
Creating a user. |
87 |
user_delete |
Deleting a user. |
88 |
user_disable |
Disabling a user. |
89 |
user_enable |
Enabling a user. |
90 |
user_change_email |
Changing user email. |
91 |
user_change_password |
Changing user password. |
92 |
user_change_name |
Changing user name. |
93 |
user_change_invoicing |
Changing user invoicing. |
94 |
user_change_tag_expiration |
Changing user tag expiration. |
95 |
user_change_metadata |
Changing user metadata. |
96 |
user_generate_client_key |
Generating a client key for a user. |
97 |
login_success |
Successful login. |
98 |
logout_success |
Successful logout. |
99 |
permanently_delete_tag |
Permanently deleting a tag. |
100 |
autoprune_tag_delete |
Auto-pruning tag deletion. |
101 |
create_namespace_autoprune_policy |
Creating namespace auto-prune policy. |
102 |
update_namespace_autoprune_policy |
Updating namespace auto-prune policy. |
103 |
delete_namespace_autoprune_policy |
Deleting namespace auto-prune policy. |
104 |
login_failure |
Failed login attempt. |
About Clair
Clair uses Common Vulnerability Scoring System (CVSS) data from the National Vulnerability Database (NVD) to enrich vulnerability data, which is a United States government repository of security-related information, including known vulnerabilities and security issues in various software components and systems. Using scores from the NVD provides Clair the following benefits:
-
Data synchronization. Clair can periodically synchronize its vulnerability database with the NVD. This ensures that it has the latest vulnerability data.
-
Matching and enrichment. Clair compares the metadata and identifiers of vulnerabilities it discovers in container images with the data from the NVD. This process involves matching the unique identifiers, such as Common Vulnerabilities and Exposures (CVE) IDs, to the entries in the NVD. When a match is found, Clair can enrich its vulnerability information with additional details from NVD, such as severity scores, descriptions, and references.
-
Severity Scores. The NVD assigns severity scores to vulnerabilities, such as the Common Vulnerability Scoring System (CVSS) score, to indicate the potential impact and risk associated with each vulnerability. By incorporating NVD’s severity scores, Clair can provide more context on the seriousness of the vulnerabilities it detects.
If Clair finds vulnerabilities from NVD, a detailed and standardized assessment of the severity and potential impact of vulnerabilities detected within container images is reported to users on the UI. CVSS enrichment data provides Clair the following benefits:
-
Vulnerability prioritization. By utilizing CVSS scores, users can prioritize vulnerabilities based on their severity, helping them address the most critical issues first.
-
Assess Risk. CVSS scores can help Clair users understand the potential risk a vulnerability poses to their containerized applications.
-
Communicate Severity. CVSS scores provide Clair users a standardized way to communicate the severity of vulnerabilities across teams and organizations.
-
Inform Remediation Strategies. CVSS enrichment data can guide Quay.io users in developing appropriate remediation strategies.
-
Compliance and Reporting. Integrating CVSS data into reports generated by Clair can help organizations demonstrate their commitment to addressing security vulnerabilities and complying with industry standards and regulations.
Documentation for installing and configuring Clair can be found in Vulnerability reporting with Clair on Project Quay.
Repository mirroring
Repository mirroring
To mirror images from external registries into your Project Quay cluster and synchronize by repository names and tags, you can use repository mirroring.
From your Project Quay cluster with repository mirroring enabled, you can perform the following:
-
Choose a repository from an external registry to mirror
-
Add credentials to access the external registry
-
Identify specific container image repository names and tags to sync
-
Set intervals at which a repository is synced
-
Check the current state of synchronization
To use the mirroring functionality, you need to perform the following actions:
-
Enable repository mirroring in the Project Quay configuration file
-
Run a repository mirroring worker
-
Create mirrored repositories
All repository mirroring configurations can be performed using the configuration tool UI or by the Project Quay API.
Repository mirroring compared to geo-replication
Project Quay geo-replication mirrors the entire image storage backend data between 2 or more different storage backends while the database is shared, for example, one Project Quay registry with two different blob storage endpoints. The primary use cases for geo-replication include the following:
-
Speeding up access to the binary blobs for geographically dispersed setups
-
Guaranteeing that the image content is the same across regions
Repository mirroring synchronizes selected repositories, or subsets of repositories, from one registry to another. The registries are distinct, with each registry having a separate database and separate image storage.
The primary use cases for mirroring include the following:
-
Independent registry deployments in different data centers or regions, where a certain subset of the overall content is supposed to be shared across the data centers and regions
-
Automatic synchronization or mirroring of selected (allowlisted) upstream repositories from external registries into a local Project Quay deployment
|
Note
|
Repository mirroring and geo-replication can be used simultaneously. |
| Feature / Capability | Geo-replication | Repository mirroring |
|---|---|---|
What is the feature designed to do? |
A shared, global registry |
Distinct, different registries |
What happens if replication or mirroring has not been completed yet? |
The remote copy is used (slower) |
No image is served |
Is access to all storage backends in both regions required? |
Yes (all Project Quay nodes) |
No (distinct storage) |
Can users push images from both sites to the same repository? |
Yes |
No |
Is all registry content and configuration identical across all regions (shared database)? |
Yes |
No |
Can users select individual namespaces or repositories to be mirrored? |
No |
Yes |
Can users apply filters to synchronization rules? |
No |
Yes |
Are individual / different role-base access control configurations allowed in each region |
No |
Yes |
Using repository mirroring
The following list shows features and limitations of Project Quay repository mirroring:
-
With repository mirroring, you can mirror an entire repository or selectively limit which images are synced. Filters can be based on a comma-separated list of tags, a range of tags, or other means of identifying tags through Unix shell-style wildcards. For more information, see the documentation for wildcards.
-
When a repository is set as mirrored, you cannot manually add other images to that repository.
-
Because the mirrored repository is based on the repository and tags you set, it will hold only the content represented by the repository and tag pair. For example if you change the tag so that some images in the repository no longer match, those images will be deleted.
-
Only the designated robot can push images to a mirrored repository, superseding any role-based access control permissions set on the repository.
-
Mirroring can be configured to rollback on failure, or to run on a best-effort basis.
-
With a mirrored repository, a user with read permissions can pull images from the repository but cannot push images to the repository.
-
Changing settings on your mirrored repository can be performed in the Project Quay user interface, using the Repositories → Mirrors tab for the mirrored repository you create.
-
Images are synced at set intervals, but can also be synced on demand.
Enabling repository mirroring
By default, FEATURE_REPO_MIRROR is set to False. To enable mirroring, you must set FEATURE_REPO_MIRROR: true in your config.yaml file.
-
Set
FEATURE_REPO_MIRROR: truein yourconfig.yamlfile. For example:# ... FEATURE_REPO_MIRROR: true # ... -
Restart your Project Quay registry.
Mirroring configuration fields
Mirroring in Project Quay enables automatic synchronization of repositories with upstream sources. This feature is useful for maintaining local mirrors of remote container images, ensuring availability in disconnected environments or improving performance through caching.
| Field | Type | Description |
|---|---|---|
FEATURE_REPO_MIRROR |
Boolean |
Enable or disable repository mirroring |
REPO_MIRROR_INTERVAL |
Number |
The number of seconds between checking for repository mirror candidates |
REPO_MIRROR_SERVER_HOSTNAME |
String |
Replaces the |
REPO_MIRROR_TLS_VERIFY |
Boolean |
Require HTTPS and verify certificates of Quay registry during mirror. |
REPO_MIRROR_ROLLBACK |
Boolean |
When set to Default: |
# ...
FEATURE_REPO_MIRROR: true
REPO_MIRROR_INTERVAL: 30
REPO_MIRROR_SERVER_HOSTNAME: "openshift-quay-service"
REPO_MIRROR_TLS_VERIFY: true
REPO_MIRROR_ROLLBACK: false
# ...Mirroring worker
Use the following procedure to start the repository mirroring worker.
-
If you have not configured TLS communications using a
/root/ca.crtcertificate, enter the following command to start aQuaypod with therepomirroroption:$ sudo podman run -d --name mirroring-worker \ -v $QUAY/config:/conf/stack:Z \ quay.io/projectquay/quay:v3.17.0 repomirror
-
If you have configured TLS communications using a
/root/ca.crtcertificate, enter the following command to start the repository mirroring worker:$ sudo podman run -d --name mirroring-worker \ -v $QUAY/config:/conf/stack:Z \ -v /root/ca.crt:/etc/pki/ca-trust/source/anchors/ca.crt:Z \ quay.io/projectquay/quay:v3.17.0 repomirror
Creating a mirrored repository
When mirroring a repository from an external container registry, you must create a new private repository. Typically, the same name is used as the target repository, for example, quay-rhel9.
Repository mirroring settings
Use the following procedure to adjust the settings of your mirrored repository.
-
You have enabled repository mirroring in your Project Quay configuration file.
-
You have deployed a mirroring worker.
-
Navigate to the Repositories page of your registry and click the name of a repository, for example, test-mirror.
-
Click Settings → Repository state.
-
Click Mirror.
-
Click the Mirroring tab and enter the details for connecting to the external registry, along with the tags, scheduling and access information:
-
Enter the details as required in the following fields:
-
Registry Location: The external repository you want to mirror, for example,
registry.redhat.io/quay/quay-rhel8. -
Tags: Enter a comma-separated list of individual tags or tag patterns. (See Tag Patterns section for details.)
-
Start Date: The date on which mirroring begins. The current date and time is used by default.
-
Sync Interval: Defaults to syncing every 24 hours. You can change that based on hours or days.
-
Skopeo timeout interval: Defaults to
300seconds (5 minutes). The maximum timeout length is43200seconds (12 hours). -
Robot User: Create a new robot account or choose an existing robot account to do the mirroring.
-
Username: The username for accessing the external registry holding the repository you are mirroring.
-
Password: The password associated with the Username. Note that the password cannot include characters that require an escape character (\).
-
-
In the Advanced Settings section, you can optionally configure SSL/TLS and proxy with the following options:
-
Verify TLS: Select this option if you want to require HTTPS and to verify certificates when communicating with the target remote registry.
-
Accept Unsigned Images: Selecting this option allows unsigned images to be mirrored.
-
HTTP Proxy: Select this option if you want to require HTTPS and to verify certificates when communicating with the target remote registry.
-
HTTPS PROXY: Identify the HTTPS proxy server needed to access the remote site, if a proxy server is needed.
-
No Proxy: List of locations that do not require proxy.
-
-
After filling out all information, click Enable Mirror.
Synchronize now
Use the following procedure to initiate the mirroring operation.
-
Navigate to the Mirroring tab of your repository.
-
Press the Sync Now button.
-
Click the Logs tab to view available logs.
-
When mirroring is complete, the image appear in the Tags tab.
Event notifications for mirroring
There are three notification events for repository mirroring:
-
Repository Mirror Started
-
Repository Mirror Success
-
Repository Mirror Unsuccessful
The events can be configured inside of the Settings tab for each repository, and all existing notification methods such as email, Slack, Quay UI, and webhooks are supported.
Mirroring tag patterns
At least one tag must be entered. The following table references possible image tag patterns.
Pattern syntax
Pattern |
Description |
* |
Matches all characters |
? |
Matches any single character |
[seq] |
Matches any character in seq |
[!seq] |
Matches any character not in seq |
Example tag patterns
Example Pattern |
Example Matches |
v3* |
v32, v3.1, v3.2, v3.2-4beta, v3.3 |
v3.* |
v3.1, v3.2, v3.2-4beta |
v3.? |
v3.1, v3.2, v3.3 |
v3.[12] |
v3.1, v3.2 |
v3.[12]* |
v3.1, v3.2, v3.2-4beta |
v3.[!1]* |
v3.2, v3.2-4beta, v3.3 |
Working with mirrored repositories
After you have created a mirrored repository, there are several ways that you can work with that repository.
Select your mirrored repository from the Repositories page to do any of the following:
-
Enable/disable the repository: Select the Mirroring button in the left column, then toggle the Enabled check box to enable or disable the repository temporarily.
-
Check mirror logs: To make sure the mirrored repository is working properly, you can check the mirror logs. To do that, select the Usage Logs button in the left column. Here’s an example:
-
Sync mirror now: To immediately sync the images in your repository, select the Sync Now button.
-
Change credentials: To change the username and password, select DELETE from the Credentials line. Then select None and add the username and password needed to log into the external registry when prompted.
-
Cancel mirroring: To stop mirroring, which keeps the current images available but stops new ones from being synced, select the CANCEL button.
-
Set robot permissions: Project Quay robot accounts are named tokens that hold credentials for accessing external repositories. By assigning credentials to a robot, that robot can be used across multiple mirrored repositories that need to access the same external registry.
You can assign an existing robot to a repository by navigating to Organizations → Robot accounts. On this page, you can view the following information:
-
Check which repositories are assigned to that robot.
-
Assign
Read,WriteorAdminprivileges to that robot from the PERMISSION field.
-
-
Change robot credentials: Robots can hold credentials such as Kubernetes secrets, Docker login information, and Podman login information. To change robot credentials, select the Options gear on the robot’s account line on the Robot Accounts window and choose View Credentials. Add the appropriate credentials for the external repository the robot needs to access.
-
Check and change general setting: Select the Settings button (gear icon) from the left column on the mirrored repository page. On the resulting page, you can change settings associated with the mirrored repository. In particular, you can change User and Robot Permissions, to specify exactly which users and robots can read from or write to the repo.
Repository mirroring recommendations
Best practices for repository mirroring include the following:
-
Repository mirroring pods can run on any node. This means that you can run mirroring on nodes where Project Quay is already running.
-
Repository mirroring is scheduled in the database and runs in batches. As a result, repository workers check each repository mirror configuration file and reads when the next sync needs to be. More mirror workers means more repositories can be mirrored at the same time. For example, running 10 mirror workers means that a user can run 10 mirroring operators in parallel. If a user only has 2 workers with 10 mirror configurations, only 2 operators can be performed.
-
The optimal number of mirroring pods depends on the following conditions:
-
The total number of repositories to be mirrored
-
The number of images and tags in the repositories and the frequency of changes
-
Parallel batching
For example, if a user is mirroring a repository that has 100 tags, the mirror will be completed by one worker. Users must consider how many repositories one wants to mirror in parallel, and base the number of workers around that.
Multiple tags in the same repository cannot be mirrored in parallel.
-
IPv6 and dual-stack deployments
Your standalone Project Quay deployment can now be served in locations that only support IPv6, such as Telco and Edge environments. Support is also offered for dual-stack networking so your Project Quay deployment can listen on IPv4 and IPv6 simultaneously.
For a list of known limitations, see IPv6 limitations
Enabling the IPv6 protocol family
Use the following procedure to enable IPv6 support on your standalone Project Quay deployment.
-
Your host and container software platform (Docker, Podman) must be configured to support IPv6.
-
In your deployment’s
config.yamlfile, add theFEATURE_LISTEN_IP_VERSIONparameter and set it toIPv6, for example:--- FEATURE_GOOGLE_LOGIN: false FEATURE_INVITE_ONLY_USER_CREATION: false FEATURE_LISTEN_IP_VERSION: IPv6 FEATURE_MAILING: false FEATURE_NONSUPERUSER_TEAM_SYNCING_SETUP: false --- -
Start, or restart, your Project Quay deployment.
-
Check that your deployment is listening to IPv6 by entering the following command:
$ curl <quay_endpoint>/health/instance {"data":{"services":{"auth":true,"database":true,"disk_space":true,"registry_gunicorn":true,"service_key":true,"web_gunicorn":true}},"status_code":200}
After enabling IPv6 in your deployment’s config.yaml, all Project Quay features can be used as normal, so long as your environment is configured to use IPv6 and is not hindered by the ipv6-limitations[current limitations].
|
Warning
|
If your environment is configured to IPv4, but the |
Enabling the dual-stack protocol family
Use the following procedure to enable dual-stack (IPv4 and IPv6) support on your standalone Project Quay deployment.
-
Your host and container software platform (Docker, Podman) must be configured to support IPv6.
-
In your deployment’s
config.yamlfile, add theFEATURE_LISTEN_IP_VERSIONparameter and set it todual-stack, for example:--- FEATURE_GOOGLE_LOGIN: false FEATURE_INVITE_ONLY_USER_CREATION: false FEATURE_LISTEN_IP_VERSION: dual-stack FEATURE_MAILING: false FEATURE_NONSUPERUSER_TEAM_SYNCING_SETUP: false --- -
Start, or restart, your Project Quay deployment.
-
Check that your deployment is listening to both channels by entering the following command:
-
For IPv4, enter the following command:
$ curl --ipv4 <quay_endpoint> {"data":{"services":{"auth":true,"database":true,"disk_space":true,"registry_gunicorn":true,"service_key":true,"web_gunicorn":true}},"status_code":200} -
For IPv6, enter the following command:
$ curl --ipv6 <quay_endpoint> {"data":{"services":{"auth":true,"database":true,"disk_space":true,"registry_gunicorn":true,"service_key":true,"web_gunicorn":true}},"status_code":200}
-
After enabling dual-stack in your deployment’s config.yaml, all Project Quay features can be used as normal, so long as your environment is configured for dual-stack.
IPv6 and dual-stack limitations
-
Currently, attempting to configure your Project Quay deployment with the common Azure Blob Storage configuration will not work on IPv6 single stack environments. Because the endpoint of Azure Blob Storage does not support IPv6, there is no workaround in place for this issue.
For more information, see PROJQUAY-4433.
-
Currently, attempting to configure your Project Quay deployment with Amazon S3 CloudFront will not work on IPv6 single stack environments. Because the endpoint of Amazon S3 CloudFront does not support IPv6, there is no workaround in place for this issue.
For more information, see PROJQUAY-4470.
LDAP Authentication Setup for Project Quay
Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Project Quay supports using LDAP as an identity provider.
Considerations when enabling LDAP
Prior to enabling LDAP for your Project Quay deployment, you should consider the following.
Existing Project Quay deployments
Conflicts between usernames can arise when you enable LDAP for an existing Project Quay deployment that already has users configured. For example, one user, alice, was manually created in Project Quay prior to enabling LDAP. If the username alice also exists in the LDAP directory, Project Quay automatically creates a new user, alice-1, when alice logs in for the first time using LDAP. Project Quay then automatically maps the LDAP credentials to the alice account. For consistency reasons, this might be erroneous for your Project Quay deployment. It is recommended that you remove any potentially conflicting local account names from Project Quay prior to enabling LDAP.
Manual User Creation and LDAP authentication
When Project Quay is configured for LDAP, LDAP-authenticated users are automatically created in Project Quay’s database on first log in, if the configuration option FEATURE_USER_CREATION is set to True. If this option is set to False, the automatic user creation for LDAP users fails, and the user is not allowed to log in. In this scenario, the superuser needs to create the desired user account first. Conversely, if FEATURE_USER_CREATION is set to True, this also means that a user can still create an account from the Project Quay login screen, even if there is an equivalent user in LDAP.
Configuring LDAP for Project Quay
You can configure LDAP for Project Quay by updating your config.yaml file directly and restarting your deployment. Use the following procedure as a reference when configuring LDAP for Project Quay.
-
Update your
config.yamlfile directly to include the following relevant information:# ... AUTHENTICATION_TYPE: LDAP (1) # ... LDAP_ADMIN_DN: uid=<name>,ou=Users,o=<organization_id>,dc=<example_domain_component>,dc=com (2) LDAP_ADMIN_PASSWD: ABC123 (3) LDAP_ALLOW_INSECURE_FALLBACK: false (4) LDAP_BASE_DN: (5) - dc=example - dc=com LDAP_EMAIL_ATTR: mail (6) LDAP_UID_ATTR: uid (7) LDAP_URI: ldap://<example_url>.com (8) LDAP_USER_FILTER: (memberof=cn=developers,ou=Users,dc=<domain_name>,dc=com) (9) LDAP_USER_RDN: (10) - ou=people LDAP_SECONDARY_USER_RDNS: (11) - ou=<example_organization_unit_one> - ou=<example_organization_unit_two> - ou=<example_organization_unit_three> - ou=<example_organization_unit_four> # ...-
Required. Must be set to
LDAP. -
Required. The admin DN for LDAP authentication.
-
Required. The admin password for LDAP authentication.
-
Required. Whether to allow SSL/TLS insecure fallback for LDAP authentication.
-
Required. The base DN for LDAP authentication.
-
Required. The email attribute for LDAP authentication.
-
Required. The UID attribute for LDAP authentication.
-
Required. The LDAP URI.
-
Required. The user filter for LDAP authentication.
-
Required. The user RDN for LDAP authentication.
-
Optional. Secondary User Relative DNs if there are multiple Organizational Units where user objects are located.
-
-
After you have added all required LDAP fields, save the changes and restart your Project Quay deployment.
Enabling the LDAP_RESTRICTED_USER_FILTER configuration field
The LDAP_RESTRICTED_USER_FILTER configuration field is a subset of the LDAP_USER_FILTER configuration field. When configured, this option allows Project Quay administrators the ability to configure LDAP users as restricted users when Project Quay uses LDAP as its authentication provider.
Use the following procedure to enable LDAP restricted users on your Project Quay deployment.
-
Your Project Quay deployment uses LDAP as its authentication provider.
-
You have configured the
LDAP_USER_FILTERfield in yourconfig.yamlfile.
-
In your deployment’s
config.yamlfile, add theLDAP_RESTRICTED_USER_FILTERparameter and specify the group of restricted users, for example,members:# ... AUTHENTICATION_TYPE: LDAP # ... FEATURE_RESTRICTED_USERS: true (1) # ... LDAP_ADMIN_DN: uid=<name>,ou=Users,o=<organization_id>,dc=<example_domain_component>,dc=com LDAP_ADMIN_PASSWD: ABC123 LDAP_ALLOW_INSECURE_FALLBACK: false LDAP_BASE_DN: - o=<organization_id> - dc=<example_domain_component> - dc=com LDAP_EMAIL_ATTR: mail LDAP_UID_ATTR: uid LDAP_URI: ldap://<example_url>.com LDAP_USER_FILTER: (memberof=cn=developers,ou=Users,o=<example_organization_unit>,dc=<example_domain_component>,dc=com) LDAP_RESTRICTED_USER_FILTER: (<filterField>=<value>) (2) LDAP_USER_RDN: - ou=<example_organization_unit> - o=<organization_id> - dc=<example_domain_component> - dc=com # ...-
Must be set to
Truewhen configuring an LDAP restricted user. -
Configures specified users as restricted users.
-
-
Start, or restart, your Project Quay deployment.
After enabling the LDAP_RESTRICTED_USER_FILTER feature, your LDAP Project Quay users are restricted from reading and writing content, and creating organizations.
Enabling the LDAP_SUPERUSER_FILTER configuration field
With the LDAP_SUPERUSER_FILTER field configured, Project Quay administrators can configure Lightweight Directory Access Protocol (LDAP) users as superusers if Project Quay uses LDAP as its authentication provider.
Use the following procedure to enable LDAP superusers on your Project Quay deployment.
-
Your Project Quay deployment uses LDAP as its authentication provider.
-
You have configured the
LDAP_USER_FILTERfield field in yourconfig.yamlfile.
-
In your deployment’s
config.yamlfile, add theLDAP_SUPERUSER_FILTERparameter and add the group of users you want configured as super users, for example,root:# ... AUTHENTICATION_TYPE: LDAP # ... LDAP_ADMIN_DN: uid=<name>,ou=Users,o=<organization_id>,dc=<example_domain_component>,dc=com LDAP_ADMIN_PASSWD: ABC123 LDAP_ALLOW_INSECURE_FALLBACK: false LDAP_BASE_DN: - o=<organization_id> - dc=<example_domain_component> - dc=com LDAP_EMAIL_ATTR: mail LDAP_UID_ATTR: uid LDAP_URI: ldap://<example_url>.com LDAP_USER_FILTER: (memberof=cn=developers,ou=Users,o=<example_organization_unit>,dc=<example_domain_component>,dc=com) LDAP_SUPERUSER_FILTER: (<filterField>=<value>) (1) LDAP_USER_RDN: - ou=<example_organization_unit> - o=<organization_id> - dc=<example_domain_component> - dc=com # ...-
Configures specified users as superusers.
-
-
Start, or restart, your Project Quay deployment.
After enabling the LDAP_SUPERUSER_FILTER feature, your LDAP Project Quay users have superuser privileges. The following options are available to superusers:
-
Manage users
-
Manage organizations
-
Manage service keys
-
View the change log
-
Query the usage logs
-
Create globally visible user messages
Common LDAP configuration issues
The following errors might be returned with an invalid configuration.
-
Invalid credentials. If you receive this error, the Administrator DN or Administrator DN password values are incorrect. Ensure that you are providing accurate Administrator DN and password values.
-
*Verification of superuser %USERNAME% failed. This error is returned for the following reasons:
-
The username has not been found.
-
The user does not exist in the remote authentication system.
-
LDAP authorization is configured improperly.
-
-
Cannot find the current logged in user. When configuring LDAP for Project Quay, there may be situations where the LDAP connection is established successfully using the username and password provided in the Administrator DN fields. However, if the current logged-in user cannot be found within the specified User Relative DN path using the UID Attribute or Mail Attribute fields, there are typically two potential reasons for this:
-
The current logged in user does not exist in the User Relative DN path.
-
The Administrator DN does not have rights to search or read the specified LDAP path.
To fix this issue, ensure that the logged in user is included in the User Relative DN path, or provide the correct permissions to the Administrator DN account.
-
LDAP configuration fields
For a full list of LDAP configuration fields, see LDAP configuration fields
Configuring OIDC for Project Quay
Configuring OpenID Connect (OIDC) for Project Quay can provide several benefits to your deployment. For example, OIDC allows users to authenticate to Project Quay using their existing credentials from an OIDC provider, such as Red Hat Single Sign-On, Google, Github, Microsoft, or others. Other benefits of OIDC include centralized user management, enhanced security, and single sign-on (SSO). Overall, OIDC configuration can simplify user authentication and management, enhance security, and provide a seamless user experience for Project Quay users.
The following procedures show you how to configure Microsoft Entra ID on a standalone deployment of Project Quay, and how to configure Red Hat Single Sign-On on an Operator-based deployment of Project Quay. These procedures are interchangeable depending on your deployment type.
|
Note
|
By following these procedures, you will be able to add any OIDC provider to Project Quay, regardless of which identity provider you choose to use. |
Configuring Microsoft Entra ID OIDC on a standalone deployment of Project Quay
By integrating Microsoft Entra ID authentication with Project Quay, your organization can take advantage of the centralized user management and security features offered by Microsoft Entra ID. Some features include the ability to manage user access to Project Quay repositories based on their Microsoft Entra ID roles and permissions, and the ability to enable multi-factor authentication and other security features provided by Microsoft Entra ID.
Azure Active Directory (Microsoft Entra ID) authentication for Project Quay allows users to authenticate and access Project Quay using their Microsoft Entra ID credentials.
Use the following procedure to configure Microsoft Entra ID by updating the Project Quay config.yaml file directly.
|
Note
|
Procedure
|
-
Use the following reference and update your
config.yamlfile with your desired OIDC provider’s credentials:AUTHENTICATION_TYPE: OIDC # ... AZURE_LOGIN_CONFIG: (1) CLIENT_ID: <client_id> (2) CLIENT_SECRET: <client_secret> (3) OIDC_SERVER: <oidc_server_address_> (4) SERVICE_NAME: Microsoft Entra ID (5) VERIFIED_EMAIL_CLAIM_NAME: <verified_email> (6) USE_PKCE: True (7) PKCE_METHOD: "S256" (8) PUBLIC_CLIENT: True (9) # ...-
The parent key that holds the OIDC configuration settings. In this example, the parent key used is
AZURE_LOGIN_CONFIG, however, the stringAZUREcan be replaced with any arbitrary string based on your specific needs, for exampleABC123.However, the following strings are not accepted:GOOGLE,GITHUB. These strings are reserved for their respective identity platforms and require a specificconfig.yamlentry contingent upon when platform you are using. -
The client ID of the application that is being registered with the identity provider.
-
The client secret of the application that is being registered with the identity provider.
-
The address of the OIDC server that is being used for authentication. In this example, you must use
sts.windows.netas the issuer identifier. Usinghttps://login.microsoftonline.comresults in the following error:Could not create provider for AzureAD. Error: oidc: issuer did not match the issuer returned by provider, expected "https://login.microsoftonline.com/73f2e714-xxxx-xxxx-xxxx-dffe1df8a5d5" got "https://sts.windows.net/73f2e714-xxxx-xxxx-xxxx-dffe1df8a5d5/". -
The name of the service that is being authenticated.
-
The name of the claim that is used to verify the email address of the user.
-
Specifies whether to enable Proof Key for Code Exchange (PKCE) for OIDC authentication. Defaults to
False. -
Specifies the code challenge method used to generate the
code_challengesent in the initial authorization request. Defaults toS256. -
Specifies whether to omit
client_secretduring token request when the client is public. Defaults toFalse.
-
-
Proper configuration of Microsoft Entra ID results three redirects with the following format:
-
https://QUAY_HOSTNAME/oauth2/<name_of_service>/callback -
https://QUAY_HOSTNAME/oauth2/<name_of_service>/callback/attach -
https://QUAY_HOSTNAME/oauth2/<name_of_service>/callback/cli
-
-
Restart your Project Quay deployment.
Configuring Red Hat Single Sign-On for Project Quay
Based on the Keycloak project, Red Hat Single Sign-On (RH-SSO) is an open source identity and access management (IAM) solution provided by Red Hat. RH-SSO allows organizations to manage user identities, secure applications, and enforce access control policies across their systems and applications. It also provides a unified authentication and authorization framework, which allows users to log in one time and gain access to multiple applications and resources without needing to re-authenticate. For more information, see Red Hat Single Sign-On.
By configuring Red Hat Single Sign-On on Project Quay, you can create a seamless authentication integration between Project Quay and other application platforms like OpenShift Container Platform.
Configuring the Red Hat Single Sign-On Operator for use with the Project Quay Operator
Use the following procedure to configure Red Hat Single Sign-On for the Project Quay Operator on OpenShift Container Platform.
-
You have set up the Red Hat Single Sign-On Operator. For more information, see Red Hat Single Sign-On Operator.
-
You have configured SSL/TLS for your Red Hat Quay on OpenShift Container Platform deployment and for Red Hat Single Sign-On.
-
You have generated a single Certificate Authority (CA) and uploaded it to your Red Hat Single Sign-On Operator and to your Project Quay configuration.
-
Navigate to the Red Hat Single Sign-On Admin Console.
-
On the OpenShift Container Platform Web Console, navigate to Network → Route.
-
Select the Red Hat Single Sign-On project from the drop-down list.
-
Find the Red Hat Single Sign-On Admin Console in the Routes table.
-
-
Select the Realm that you will use to configure Project Quay.
-
Click Clients under the Configure section of the navigation panel, and then click the Create button to add a new OIDC for Project Quay.
-
Enter the following information.
-
Client ID:
quay-enterprise -
Client Protocol:
openid-connect -
Root URL:
https://<quay_endpoint>/
-
-
Click Save. This results in a redirect to the Clients setting panel.
-
Navigate to Access Type and select Confidential.
-
Navigate to Valid Redirect URIs. You must provide three redirect URIs. The value should be the fully qualified domain name of the Project Quay registry appended with
/oauth2/redhatsso/callback. For example:-
https://<quay_endpoint>/oauth2/redhatsso/callback -
https://<quay_endpoint>/oauth2/redhatsso/callback/attach -
https://<quay_endpoint>/oauth2/redhatsso/callback/cli
-
-
Click Save and navigate to the new Credentials setting.
-
Copy the value of the Secret.
Configuring the Project Quay Operator to use Red Hat Single Sign-On
Use the following procedure to configure Red Hat Single Sign-On with the Project Quay Operator.
-
You have set up the Red Hat Single Sign-On Operator. For more information, see Red Hat Single Sign-On Operator.
-
You have configured SSL/TLS for your Red Hat Quay on OpenShift Container Platform deployment and for Red Hat Single Sign-On.
-
You have generated a single Certificate Authority (CA) and uploaded it to your Red Hat Single Sign-On Operator and to your Project Quay configuration.
-
Edit your Project Quay
config.yamlfile by navigating to Operators → Installed Operators → Red Hat Quay → Quay Registry → Config Bundle Secret. Then, click Actions → Edit Secret. Alternatively, you can update theconfig.yamlfile locally. -
Add the following information to your Red Hat Quay on OpenShift Container Platform
config.yamlfile:# ... RHSSO_LOGIN_CONFIG: CLIENT_ID: <client_id> CLIENT_SECRET: <client_secret> OIDC_SERVER: <oidc_server_url> SERVICE_NAME: <service_name> SERVICE_ICON: <service_icon> VERIFIED_EMAIL_CLAIM_NAME: <example_email_address> PREFERRED_USERNAME_CLAIM_NAME: <preferred_username> LOGIN_SCOPES: [ 'openid', 'roles' ] USE_PKCE: true PKCE_METHOD: "S256" # ...where:
RHSSO_LOGIN_CONFIG::Specifies the parent key that holds the OIDC configuration settings. In this example, the parent key used isRHSSO_LOGIN_CONFIGand the string can be replaced with any arbitrary string based on your specific needs, for exampleABC123. However, the stringsGOOGLEANDGITHUBare not accepted. These strings are reserved for their respective identity platforms and require a specificconfig.yamlentry contingent upon when platform you are using.CLIENT_ID::Specifies The client ID of the application that is being registered with the identity provider. For example,quay.CLIENT_SECRET::Specifies client secret.OIDC_SERVER::Specifies the fully qualified domain name (FQDN) of the Red Hat Single Sign-On instance, appended with/auth/realms/and the Realm name. You must include the forward slash at the end, for example,https://sso-redhat.example.com//auth/realms/<your_realm_name>/.SERVICE_NAME::Specifies the name that is displayed on the Project Quay login page, for example,Red hat Single Sign On.SERVICE_ICON::Specifies the icon on the login screen. For example,/static/img/RedHat.svg.VERIFIED_EMAIL_CLAIM_NAME::Specifies the name of the claim that is used to verify the email address of the user.PREFERRED_USERNAME_CLAIM_NAME::Specifies the name of the claim that is used to verify the email address of the user.LOGIN_SCOPES::Specifies the scopes to send to the OIDC provider when performing the login flow, for example,openid.USE_PKCE::Specifies whether to enable Proof Key for Code Exchange (PKCE). Defaults toFalse.PKCE_METHOD::Specifies the code challenge method used to generate thecode_challengesent in the initial authorization request. Defaults toS256. -
Restart your Red Hat Quay on OpenShift Container Platform deployment with Red Hat Single Sign-On enabled.
Team synchronization for Project Quay OIDC deployments
Administrators can leverage an OpenID Connect (OIDC) identity provider that supports group or team synchronization to apply repository permissions to sets of users in Project Quay. This allows administrators to avoid having to manually create and sync group definitions between Project Quay and the OIDC group.
Enabling synchronization for Project Quay OIDC deployments
Use the following procedure to enable team synchronization when your Project Quay deployment uses an OIDC authenticator.
|
Important
|
The following procedure does not use a specific OIDC provider. Instead, it provides a general outline of how best to approach team synchronization between an OIDC provider and Project Quay. Any OIDC provider can be used to enable team synchronization, however, setup might vary depending on your provider. |
-
Update your
config.yamlfile with the following information:AUTHENTICATION_TYPE: OIDC # ... OIDC_LOGIN_CONFIG: CLIENT_ID: (1) CLIENT_SECRET: (2) OIDC_SERVER: (3) SERVICE_NAME: (4) PREFERRED_GROUP_CLAIM_NAME: (5) LOGIN_SCOPES: [ 'openid', '<example_scope>' ] (6) OIDC_DISABLE_USER_ENDPOINT: false (7) # ... FEATURE_TEAM_SYNCING: true (8) FEATURE_NONSUPERUSER_TEAM_SYNCING_SETUP: true (9) FEATURE_UI_V2: true # ...-
Required. The registered OIDC client ID for this Project Quay instance.
-
Required. The registered OIDC client secret for this Project Quay instance.
-
Required. The address of the OIDC server that is being used for authentication. This URL should be such that a
GETrequest to<OIDC_SERVER>/.well-known/openid-configurationreturns the provider’s configuration information. This configuration information is essential for the relying party (RP) to interact securely with the OpenID Connect provider and obtain necessary details for authentication and authorization processes. -
Required. The name of the service that is being authenticated.
-
Required. The key name within the OIDC token payload that holds information about the user’s group memberships. This field allows the authentication system to extract group membership information from the OIDC token so that it can be used with Project Quay.
-
Required. Adds additional scopes that Project Quay uses to communicate with the OIDC provider. Must include
'openid'. Additional scopes are optional. -
Whether to allow or disable the
/userinfoendpoint. If using Azure Entra ID, set this field toTrue. Defaults toFalse. -
Required. Whether to allow for team membership to be synced from a backing group in the authentication engine.
-
Optional. If enabled, non-superusers can setup team synchronization.
-
-
Restart your Project Quay registry.
Setting up your Project Quay deployment for team synchronization
-
Log in to your Project Quay registry via your OIDC provider.
-
On the Project Quay v2 UI dashboard, click Create Organization.
-
Enter and Organization name, for example,
test-org. -
Click the name of the Organization.
-
In the navigation pane, click Teams and membership.
-
Click Create new team and enter a name, for example,
testteam. -
On the Create team pop-up:
-
Optional. Add this team to a repository.
-
Add a team member, for example,
user1, by typing in the user’s account name. -
Add a robot account to this team. This page provides the option to create a robot account.
-
-
Click Next.
-
On the Review and Finish page, review the information that you have provided and click Review and Finish.
-
To enable team synchronization for your Project Quay OIDC deployment, click Enable Directory Sync on the Teams and membership page.
-
You are prompted to enter the group Object ID if your OIDC authenticator is Azure Entra ID, or the group name if using a different provider. Note the message in the popup:
WarningPlease note that once team syncing is enabled, the membership of users who are already part of the team will be revoked. OIDC group will be the single source of truth. This is a non-reversible action. Team’s user membership from within Quay will be ready-only.
-
Click Enable Sync.
-
You are returned to the Teams and membership page. Note that users of this team are removed and are re-added upon logging back in. At this stage, only the robot account is still part of the team.
A banner at the top of the page confirms that the team is synced:
This team is synchronized with a group in OIDC and its user membership is therefore read-only.By clicking the Directory Synchronization Config accordion, the OIDC group that your deployment is synchronized with appears.
-
Log out of your Project Quay registry and continue on to the verification steps.
Use the following verification procedure to ensure that user1 appears as a member of the team.
-
Log back in to your Project Quay registry.
-
Click Organizations → test-org → test-team Teams and memberships.
user1now appears as a team member for this team.
Use the following procedure to remove user1 from a group via your OIDC provider, and subsequently remove them from the team on Project Quay.
-
Navigate to your OIDC provider’s administration console.
-
Navigate to the Users page of your OIDC provider. The name of this page varies depending on your provider.
-
Click the name of the user associated with Project Quay, for example,
user1. -
Remove the user from group in the configured identity provider.
-
Remove, or unassign, the access permissions from the user.
-
Log in to your Project Quay registry.
-
Click Organizations → test-org → test-team Teams and memberships.
user1has been removed from this team.
Keyless authentication with robot accounts
In previous versions of Project Quay, robot account tokens were valid for the lifetime of the token unless deleted or regenerated. Tokens that do not expire have security implications for users who do not want to store long-term passwords or manage the deletion, or regeneration, or new authentication tokens.
With Project Quay 3.17, Project Quay administrators are provided the ability to exchange external OIDC tokens for short-lived, or ephemeral robot account tokens with either Red Hat Single Sign-On (based on the Keycloak project) or Microsoft Entra ID. This allows robot accounts to leverage tokens that last one hour, which are are refreshed regularly and can be used to authenticate individual transactions.
This feature greatly enhances the security of your Project Quay registry by mitigating the possibility of robot token exposure by removing the tokens after one hour.
Configuring keyless authentication with robot accounts is a multi-step procedure that requires setting a robot federation, generating an OAuth2 token from your OIDC provider, and exchanging the OAuth2 token for a robot account access token.
Generating an OAuth2 token with Red Hat Sign Sign-On
The following procedure shows you how to generate an OAuth2 token using Red Hat Single Sign-On. Depending on your OIDC provider, these steps will vary.
-
On the Red Hat Single Sign-On UI:
-
Click Clients and then the name of the application or service that can request authentication of a user.
-
On the Settings page of your client, ensure that the following options are set or enabled:
-
Client ID
-
Valid redirect URI
-
Client authentication
-
Authorization
-
Standard flow
-
Direct access grants
NoteSettings can differ depending on your setup.
-
-
On the Credentials page, store the Client Secret for future use.
-
On the Users page, click Add user and enter a username, for example,
service-account-quaydev. Then, click Create. -
Click the name of of the user, for example service-account-quaydev on the Users page.
-
Click the Credentials tab → Set password → and provide a password for the user. If warranted, you can make this password temporary by selecting the Temporary option.
-
Click the Realm settings tab → OpenID Endpoint Configuration. Store the
/protocol/openid-connect/tokenendpoint. For example:http://localhost:8080/realms/master/protocol/openid-connect/token
-
-
On a web browser, navigate to the following URL:
http://<keycloak_url>/realms/<realm_name>/protocol/openid-connect/auth?response_type=code&client_id=<client_id> -
When prompted, log in with the service-account-quaydev user and the temporary password you set. Complete the login by providing the required information and setting a permanent password if necessary.
-
You are redirected to the URI address provided for your client. For example:
https://localhost:3000/cb?session_state=5c9bce22-6b85-4654-b716-e9bbb3e755bc&iss=http%3A%2F%2Flocalhost%3A8080%2Frealms%2Fmaster&code=ea5b76eb-47a5-4e5d-8f71-0892178250db.5c9bce22-6b85-4654-b716-e9bbb3e755bc.cdffafbc-20fb-42b9-b254-866017057f43Take note of the
codeprovided in the address. For example:code=ea5b76eb-47a5-4e5d-8f71-0892178250db.5c9bce22-6b85-4654-b716-e9bbb3e755bc.cdffafbc-20fb-42b9-b254-866017057f43NoteThis is a temporary code that can only be used one time. If necessary, you can refresh the page or revisit the URL to obtain another code.
-
On your terminal, use the following
curl -X POSTcommand to generate a temporary OAuth2 access token:$ curl -X POST "http://localhost:8080/realms/master/protocol/openid-connect/token" (1) -H "Content-Type: application/x-www-form-urlencoded" \ -d "client_id=quaydev" (2) -d "client_secret=g8gPsBLxVrLo2PjmZkYBdKvcB9C7fmBz" (3) -d "grant_type=authorization_code" -d "code=ea5b76eb-47a5-4e5d-8f71-0892178250db.5c9bce22-6b85-4654-b716-e9bbb3e755bc.cdffafbc-20fb-42b9-b254-866017057f43" (4)-
The
protocol/openid-connect/tokenendpoint found on the Realm settings page of the Red Hat Single Sign-On UI. -
The Client ID used for this procedure.
-
The Client Secret for the Client ID.
-
The code returned from the redirect URI.
Example output{"access_token":"eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJTVmExVHZ6eDd2cHVmc1dkZmc1SHdua1ZDcVlOM01DN1N5T016R0QwVGhVIn0...", "expires_in":60,"refresh_expires_in":1800,"refresh_token":"eyJhbGciOiJIUzUxMiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJiNTBlZTVkMS05OTc1LTQwMzUtYjNkNy1lMWQ5ZTJmMjg0MTEifQ.oBDx6B3pUkXQO8m-M3hYE7v-w25ak6y70CQd5J8f5EuldhvTwpWrC1K7yOglvs09dQxtq8ont12rKIoCIi4WXw","token_type":"Bearer","not-before-policy":0,"session_state":"5c9bce22-6b85-4654-b716-e9bbb3e755bc","scope":"profile email"}
-
-
Store the
access_tokenfrom the previously step, as it will be exchanged for a Project Quay robot account token in the following procedure.
Setting up a robot account federation by using the Project Quay v2 UI
The following procedure shows you how to set up a robot account federation by using the Project Quay v2 UI. This procedure uses Red Hat Single Sign-On, which is based on the Keycloak project. These steps, and the information used to set up a robot account federation, will vary depending on your OIDC provider.
-
You have created an organization. The following example uses
fed_test. -
You have created a robot account. The following example uses
fest_test+robot1. -
You have configured a OIDC for your Project Quay deployment. The following example uses Red Hat Single Sign-On.
-
On the Red Hat Single Sign-On main page:
-
Select the appropriate realm that is authenticated for use with Project Quay. Store the issuer URL, for example,
https://keycloak-auth-realm.quayadmin.org/realms/quayrealm. -
Click Users → the name of the user to be linked with the robot account for authentication. You must use the same user account that you used when generating the OAuth2 access token.
-
On the Details page, store the ID of the user, for example,
449e14f8-9eb5-4d59-a63e-b7a77c75f770.NoteThe information collected in this step will vary depending on your OIDC provider. For example, with Red Hat Single Sign-On, the ID of a user is used as the Subject to set up the robot account federation in a subsequent step. For a different OIDC provider, like Microsoft Entra ID, this information is stored as the Subject.
-
-
On your Project Quay registry:
-
Navigate to Organizations and click the name of your organization, for example, fed_test.
-
Click Robot Accounts.
-
Click the menu kebab → Set robot federation.
-
Click the + symbol.
-
In the popup window, include the following information:
-
Issuer URL:
https://keycloak-auth-realm.quayadmin.org/realms/quayrealm. For Red Hat Single Sign-On, this is the URL of your Red Hat Single Sign-On realm. This might vary depending on your OIDC provider. -
Subject:
449e14f8-9eb5-4d59-a63e-b7a77c75f770. For Red Hat Single Sign-On, the Subject is the ID of your Red Hat Single Sign-On user. This varies depending on your OIDC provider. For example, if you are using Microsoft Entra ID, the Subject will be the Subject or your Entra ID user.
-
-
Click Save.
-
Exchanging an OAuth2 access token for a Project Quay robot account token
The following procedure leverages the access token generated in the previous procedure to create a new Project Quay robot account token. The new Project Quay robot account token is used for authentication between your OIDC provider and Project Quay.
|
Note
|
The following example uses a Python script to exchange the OAuth2 access token for a Project Quay robot account token. |
-
You have the
python3CLI tool installed.
-
Save the following Python script in a
.pyfile, for example,robot_fed_token_auth.pyimport requests import os TOKEN=os.environ.get('TOKEN') robot_user = "fed-test+robot1" def get_quay_robot_token(fed_token): URL = "https://<quay-server.example.com>/oauth2/federation/robot/token" response = requests.get(URL, auth=(robot_user,fed_token)) (1) print(response) print(response.text) if __name__ == "__main__": get_quay_robot_token(TOKEN)-
If your Project Quay deployment is using custom SSL/TLS certificates, the response must be
response = requests.get(URL,auth=(robot_user,fed_token),verify=False), which includes theverify=Falseflag.
-
-
Export the OAuth2 access token as
TOKEN. For example:$ export TOKEN = eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJTVmExVHZ6eDd2cHVmc1dkZmc1SHdua1ZDcVlOM01DN1N5T016R0QwVGhVIn0... -
Run the
robot_fed_token_auth.pyscript by entering the following command:$ python3 robot_fed_token_auth.pyExample output<Response [200]> {"token": "string..."}ImportantThis token expires after one hour. After one hour, a new token must be generated.
-
Export the robot account access token as
QUAY_TOKEN. For example:$ export QUAY_TOKEN=291cmNlX2FjY2VzcyI6eyJhY2NvdW50Ijp7InJvbGVzIjpbIm1hbmFnZS1hY2NvdW50IiwibWFuYWdlLWFjY291bnQtbGlua3MiLCJ2aWV3LXByb2ZpbGUiXX19LCJzY29wZSI6InByb2ZpbGUgZW1haWwiLCJlbWFpbF92ZXJpZ
Pushing and pulling images
After you have generated a new robot account access token and exported it, you can log in and the robot account using the access token and push and pull images.
-
You have exported the OAuth2 access token into a new robot account access token.
-
Log in to your Project Quay registry using the
fest_test+robot1robot account and theQUAY_TOKENaccess token. For example:$ podman login <quay-server.example.com> -u fed_test+robot1 -p $QUAY_TOKEN -
Pull an image from a Project Quay repository for which the robot account has the proper permissions. For example:
$ podman pull <quay-server.example.com/<repository_name>/<image_name>>Example outputGetting image source signatures Copying blob 900e6061671b done Copying config 8135583d97 done Writing manifest to image destination Storing signatures 8135583d97feb82398909c9c97607159e6db2c4ca2c885c0b8f590ee0f9fe90d 0.57user 0.11system 0:00.99elapsed 68%CPU (0avgtext+0avgdata 78716maxresident)k 800inputs+15424outputs (18major+6528minor)pagefaults 0swaps -
Attempt to pull an image from a Project Quay repository for which the robot account does not have the proper permissions. For example:
$ podman pull <quay-server.example.com/<different_repository_name>/<image_name>>Example outputError: initializing source docker://quay-server.example.com/example_repository/busybox:latest: reading manifest in quay-server.example.com/example_repository/busybox: unauthorized: access to the requested resource is not authorizedAfter one hour, the credentials for this robot account are set to expire. Afterwards, you must generate a new access token for this robot account.
Configuring AWS STS for Project Quay
AWS Security Token Service (STS) is a web service for requesting temporary, limited-privilege credentials for AWS IAM users. You can configure AWS STS with Project Quay to authenticate with Amazon S3 using temporary credentials.
AWS STS enhances security and ensures proper authentication and authorization for object storage access. It is available for standalone Project Quay deployments, Red Hat Quay on OpenShift Container Platform, and Project Quay on Red Hat OpenShift Service on AWS (ROSA). AWS STS is useful for clusters using Amazon S3 as an object storage. It allows Project Quay to use STS protocols to authenticate with Amazon S3, which can enhance the overall security of the cluster and help to ensure that access to sensitive data is properly authenticated and authorized.
Configuring AWS STS for OpenShift Container Platform or ROSA requires creating an AWS IAM user, creating an S3 role, and configuring your Project Quay config.yaml file to include the proper resources.
Configuring Project Quay to use AWS STS
Use the following procedure to edit your Project Quay config.yaml file to use AWS STS.
-
Update your
config.yamlfile for Project Quay to include the following information:# ... DISTRIBUTED_STORAGE_CONFIG: default: - STSS3Storage - sts_role_arn: <role_arn> (1) s3_bucket: <s3_bucket_name> (2) storage_path: <storage_path> (3) s3_region: <region> (4) sts_user_access_key: <s3_user_access_key> (5) sts_user_secret_key: <s3_user_secret_key> (6) # ...-
The unique Amazon Resource Name (ARN) required when configuring AWS STS
-
The name of your s3 bucket.
-
The storage path for data. Usually
/datastorage. -
The Amazon Web Services region. Defaults to
us-east-1. -
The generated AWS S3 user access key required when configuring AWS STS.
-
The generated AWS S3 user secret key required when configuring AWS STS.
-
-
Restart your Project Quay deployment.
-
Tag a sample image, for example,
busybox, that will be pushed to the repository. For example:$ podman tag docker.io/library/busybox <quay-server.example.com>/<organization_name>/busybox:test -
Push the sample image by running the following command:
$ podman push <quay-server.example.com>/<organization_name>/busybox:test -
Verify that the push was successful by navigating to the Organization that you pushed the image to in your Project Quay registry → Tags.
-
Navigate to the Amazon Web Services (AWS) console and locate your s3 bucket.
-
Click the name of your s3 bucket.
-
On the Objects page, click datastorage/.
-
On the datastorage/ page, the following resources should seen:
-
sha256/
-
uploads/
These resources indicate that the push was successful, and that AWS STS is properly configured.
-
Prometheus and Grafana metrics under Project Quay
Project Quay exports a Prometheus- and Grafana-compatible endpoint on each instance to allow for easy monitoring and alerting.
Exposing the Prometheus endpoint
Standalone Project Quay
When using podman run to start the Quay container, expose the metrics port 9091:
$ sudo podman run -d --rm -p 80:8080 -p 443:8443 -p 9091:9091\ --name=quay \ -v $QUAY/config:/conf/stack:Z \ -v $QUAY/storage:/datastorage:Z \ quay.io/projectquay/quay:v3.17.0
The metrics will now be available:
$ curl quay.example.com:9091/metricsSee Monitoring Quay with Prometheus and Grafana for details on configuring Prometheus and Grafana to monitor Quay repository counts.
Project Quay Operator
Determine the cluster IP for the quay-metrics service:
$ oc get services -n quay-enterprise
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
example-registry-clair-app ClusterIP 172.30.61.161 <none> 80/TCP,8089/TCP 18h
example-registry-clair-postgres ClusterIP 172.30.122.136 <none> 5432/TCP 18h
example-registry-quay-app ClusterIP 172.30.72.79 <none> 443/TCP,80/TCP,8081/TCP,55443/TCP 18h
example-registry-quay-config-editor ClusterIP 172.30.185.61 <none> 80/TCP 18h
example-registry-quay-database ClusterIP 172.30.114.192 <none> 5432/TCP 18h
example-registry-quay-metrics ClusterIP 172.30.37.76 <none> 9091/TCP 18h
example-registry-quay-redis ClusterIP 172.30.157.248 <none> 6379/TCP 18hConnect to your cluster and access the metrics using the cluster IP and port for the quay-metrics service:
$ oc debug node/master-0
sh-4.4# curl 172.30.37.76:9091/metrics
# HELP go_gc_duration_seconds A summary of the pause duration of garbage collection cycles.
# TYPE go_gc_duration_seconds summary
go_gc_duration_seconds{quantile="0"} 4.0447e-05
go_gc_duration_seconds{quantile="0.25"} 6.2203e-05
...Setting up Prometheus to consume metrics
Prometheus needs a way to access all Project Quay instances running in a cluster. In the typical setup, this is done by listing all the Project Quay instances in a single named DNS entry, which is then given to Prometheus.
DNS configuration under Kubernetes
A simple Kubernetes service can be configured to provide the DNS entry for Prometheus.
DNS configuration for a manual cluster
SkyDNS is a simple solution for managing this DNS record when not using Kubernetes. SkyDNS can run on an etcd cluster. Entries for each Project Quay instance in the cluster can be added and removed in the etcd store. SkyDNS will regularly read them from there and update the list of Quay instances in the DNS record accordingly.
Introduction to metrics
Project Quay provides metrics to help monitor the registry, including metrics for general registry usage, uploads, downloads, garbage collection, and authentication.
General registry statistics
General registry statistics can indicate how large the registry has grown.
| Metric name | Description |
|---|---|
quay_user_rows |
Number of users in the database |
quay_robot_rows |
Number of robot accounts in the database |
quay_org_rows |
Number of organizations in the database |
quay_repository_rows |
Number of repositories in the database |
quay_security_scanning_unscanned_images_remaining_total |
Number of images that are not scanned by the latest security scanner |
# HELP quay_user_rows number of users in the database
# TYPE quay_user_rows gauge
quay_user_rows{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="65",process_name="globalpromstats.py"} 3
# HELP quay_robot_rows number of robot accounts in the database
# TYPE quay_robot_rows gauge
quay_robot_rows{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="65",process_name="globalpromstats.py"} 2
# HELP quay_org_rows number of organizations in the database
# TYPE quay_org_rows gauge
quay_org_rows{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="65",process_name="globalpromstats.py"} 2
# HELP quay_repository_rows number of repositories in the database
# TYPE quay_repository_rows gauge
quay_repository_rows{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="65",process_name="globalpromstats.py"} 4
# HELP quay_security_scanning_unscanned_images_remaining number of images that are not scanned by the latest security scanner
# TYPE quay_security_scanning_unscanned_images_remaining gauge
quay_security_scanning_unscanned_images_remaining{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 5Queue items
The queue items metrics provide information on the multiple queues used by Quay for managing work.
| Metric name | Description |
|---|---|
quay_queue_items_available |
Number of items in a specific queue |
quay_queue_items_locked |
Number of items that are running |
quay_queue_items_available_unlocked |
Number of items that are waiting to be processed |
-
queue_name: The name of the queue. One of:
-
exportactionlogs: Queued requests to export action logs. These logs are then processed and put in storage. A link is then sent to the requester via email.
-
namespacegc: Queued namespaces to be garbage collected
-
notification: Queue for repository notifications to be sent out
-
repositorygc: Queued repositories to be garbage collected
-
secscanv4: Notification queue specific for Clair V4
-
dockerfilebuild: Queue for Quay docker builds
-
imagestoragereplication: Queued blob to be replicated across multiple storages
-
chunk_cleanup: Queued blob segments that needs to be deleted. This is only used by some storage implementations, for example, Swift.
-
For example, the queue labelled repositorygc contains the repositories marked for deletion by the repository garbage collection worker. For metrics with a queue_name label of repositorygc:
-
quay_queue_items_locked is the number of repositories currently being deleted.
-
quay_queue_items_available_unlocked is the number of repositories waiting to get processed by the worker.
# HELP quay_queue_items_available number of queue items that have not expired
# TYPE quay_queue_items_available gauge
quay_queue_items_available{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="63",process_name="exportactionlogsworker.py",queue_name="exportactionlogs"} 0
...
# HELP quay_queue_items_available_unlocked number of queue items that have not expired and are not locked
# TYPE quay_queue_items_available_unlocked gauge
quay_queue_items_available_unlocked{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="63",process_name="exportactionlogsworker.py",queue_name="exportactionlogs"} 0
...
# HELP quay_queue_items_locked number of queue items that have been acquired
# TYPE quay_queue_items_locked gauge
quay_queue_items_locked{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="63",process_name="exportactionlogsworker.py",queue_name="exportactionlogs"} 0Garbage collection metrics
These metrics show you how many resources have been removed from garbage collection (gc). They show many times the gc workers have run and how many namespaces, repositories, and blobs were removed.
| Metric name | Description |
|---|---|
quay_gc_iterations_total |
Number of iterations by the GCWorker |
quay_gc_namespaces_purged_total |
Number of namespaces purged by the NamespaceGCWorker |
quay_gc_repos_purged_total |
Number of repositories purged by the RepositoryGCWorker or NamespaceGCWorker |
quay_gc_storage_blobs_deleted_total |
Number of storage blobs deleted |
# TYPE quay_gc_iterations_created gauge
quay_gc_iterations_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.6317823190189714e+09
...
# HELP quay_gc_iterations_total number of iterations by the GCWorker
# TYPE quay_gc_iterations_total counter
quay_gc_iterations_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
...
# TYPE quay_gc_namespaces_purged_created gauge
quay_gc_namespaces_purged_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.6317823190189433e+09
...
# HELP quay_gc_namespaces_purged_total number of namespaces purged by the NamespaceGCWorker
# TYPE quay_gc_namespaces_purged_total counter
quay_gc_namespaces_purged_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
....
# TYPE quay_gc_repos_purged_created gauge
quay_gc_repos_purged_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.631782319018925e+09
...
# HELP quay_gc_repos_purged_total number of repositories purged by the RepositoryGCWorker or NamespaceGCWorker
# TYPE quay_gc_repos_purged_total counter
quay_gc_repos_purged_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
...
# TYPE quay_gc_storage_blobs_deleted_created gauge
quay_gc_storage_blobs_deleted_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.6317823190189059e+09
...
# HELP quay_gc_storage_blobs_deleted_total number of storage blobs deleted
# TYPE quay_gc_storage_blobs_deleted_total counter
quay_gc_storage_blobs_deleted_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
...Multipart uploads metrics
The multipart uploads metrics show the number of blobs uploads to storage (S3, Rados, GoogleCloudStorage, RHOCS). These can help identify issues when Quay is unable to correctly upload blobs to storage.
| Metric name | Description |
|---|---|
quay_multipart_uploads_started_total |
Number of multipart uploads to Quay storage that started |
quay_multipart_uploads_completed_total |
Number of multipart uploads to Quay storage that completed |
# TYPE quay_multipart_uploads_completed_created gauge
quay_multipart_uploads_completed_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.6317823308284895e+09
...
# HELP quay_multipart_uploads_completed_total number of multipart uploads to Quay storage that completed
# TYPE quay_multipart_uploads_completed_total counter
quay_multipart_uploads_completed_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
# TYPE quay_multipart_uploads_started_created gauge
quay_multipart_uploads_started_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.6317823308284352e+09
...
# HELP quay_multipart_uploads_started_total number of multipart uploads to Quay storage that started
# TYPE quay_multipart_uploads_started_total counter
quay_multipart_uploads_started_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
...Image push / pull metrics
A number of metrics are available related to pushing and pulling images.
Image pulls total
| Metric name | Description |
|---|---|
quay_registry_image_pulls_total |
The number of images downloaded from the registry. |
-
protocol: the registry protocol used (should always be v2)
-
ref: ref used to pull - tag, manifest
-
status: http return code of the request
Image bytes pulled
| Metric name | Description |
|---|---|
quay_registry_image_pulled_estimated_bytes_total |
The number of bytes downloaded from the registry |
-
protocol: the registry protocol used (should always be v2)
Image pushes total
| Metric name | Description |
|---|---|
quay_registry_image_pushes_total |
The number of images uploaded from the registry. |
-
protocol: the registry protocol used (should always be v2)
-
pstatus: http return code of the request
-
pmedia_type: the uploaded manifest type
Image bytes pushed
| Metric name | Description |
|---|---|
quay_registry_image_pushed_bytes_total |
The number of bytes uploaded to the registry |
# HELP quay_registry_image_pushed_bytes_total number of bytes pushed to the registry
# TYPE quay_registry_image_pushed_bytes_total counter
quay_registry_image_pushed_bytes_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="221",process_name="registry:application"} 0
...Authentication metrics
The authentication metrics provide the number of authentication requests, labeled by type and whether it succeeded or not. For example, this metric could be used to monitor failed basic authentication requests.
| Metric name | Description |
|---|---|
quay_authentication_attempts_total |
Number of authentication attempts across the registry and API |
-
auth_kind: The type of auth used, including:
-
basic
-
oauth
-
credentials
-
-
success: true or false
# TYPE quay_authentication_attempts_created gauge
quay_authentication_attempts_created{auth_kind="basic",host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="221",process_name="registry:application",success="True"} 1.6317843039374158e+09
...
# HELP quay_authentication_attempts_total number of authentication attempts across the registry and API
# TYPE quay_authentication_attempts_total counter
quay_authentication_attempts_total{auth_kind="basic",host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="221",process_name="registry:application",success="True"} 2
...Project Quay quota management and enforcement overview
With Project Quay, administrators with superuser privileges have the ability to report storage consumption and to contain registry growth by establishing configured storage quota limits. Project Quay superusers can manage the capacity limits of their environment in the following ways:
-
Quota reporting: With this setting, an administrator can track the storage consumption of all of their organizations. Additionally, users can track the storage consumption of their assigned organization.
-
Quota management: With this setting, an administrator can define soft and hard checks for Project Quay users. Soft checks tell users if the storage consumption of an organization reaches their configured threshold. Hard checks prevent users from pushing to the registry when storage consumption reaches the configured limit.
Quota can be set for the entire registry, or for a specific repository within the registry.
Collectively, these features allow service owners of a Project Quay registry to define service level agreements and support a healthy resource budget.
Quota management limitations
One limitation of the quota management feature is that calculating resource consumption on the push of an artifact results in the calculation becoming part of the push’s critical path. Without this, usage data might drift.
The maximum storage quota size is dependent on the selected database:
| Variable | Description |
|---|---|
Postgres |
8388608 TB |
MySQL |
8388608 TB |
SQL Server |
16777216 TB |
Setting a system-wide default quota
To specify a system-wide default storage quota that is applied to every organization and user, you can use the DEFAULT_SYSTEM_REJECT_QUOTA_BYTES configuration flag. When this field is set, and the quota limit has been met, the system automatically rejects new artifacts. By default, this configuration field is disabled.
If you configure a specific quota for an organization or user, and then delete that quota, the system-wide default quota applies if one has been set. Similarly, if you have configured a specific quota for an organization or user, and then modify the system-wide default quota, the updated system-wide default overrides any specific settings.
The following procedure shows you how to configure a system-wide default quota.
-
Set a system-wide default storage quota by including the
DEFAULT_SYSTEM_REJECT_QUOTA_BYTESfield in yourconfig.yamlfile. For example:# ... DEFAULT_SYSTEM_REJECT_QUOTA_BYTES: 100gb # ... -
Restart your Project Quay registry.
Establishing quota for an organization by using the Project Quay UI
The following procedure describes how you can report storage consumption and establish storage quota limits for a repository.
-
A superuser account.
-
Enough storage to meet the demands of quota limitations.
-
Set
FEATURE_QUOTA_MANAGEMENT: Truein yourconfig.yamlfile and then restart your registry. For example:# ... FEATURE_QUOTA_MANAGEMENT: True # ... -
Create a new organization or choose an existing one.
-
Log in to the registry as a superuser and navigate to the Manage Organizations tab on the Super User Admin Panel. Click the Options icon of the organization for which you want to create storage quota limits.
-
Click Configure Quota.
-
For Set storage quota, enter the initial quota, for example, 10 MiB. Then, click Apply.
-
Optional: For Quota policy select one of the following Actions. Then, enter a Quota Threshold and click Add Limit.
-
Reject: When this option is selected, any artifact that exceeds the established quota is rejected.
-
Warning: When this option is selected, users are notified of pushed artifacts that exceed the configured quota, however, the artifact successfully pushes.
NoteThe quota threshold percent determines when Project Quay starts warning users that the repository is approaching its assigned storage quota.
-
-
Pull a sample artifact by entering the following command:
$ podman pull busybox -
Tag the sample artifact by entering the following command:
$ podman tag docker.io/library/busybox quay-server.example.com/testorg/busybox:test -
Push the sample artifact to the organization by entering the following command:
$ podman push --tls-verify=false quay-server.example.com/testorg/busybox:test -
Navigate to the Super User Admin Panel on the Project Quay UI, then click Manage Organizations. The Organizations page shows the total proportion of the quota used by the artifact.
-
Optional: Pull a second sample artifact with intentions of exceeding the established quota by entering the following command:
$ podman pull nginx -
Optional: Tag the second artifact by entering the following command:
$ podman tag docker.io/library/nginx quay-server.example.com/testorg/nginx -
Optional: Push the second artifact to the organization by entering the following command:
$ podman push --tls-verify=false quay-server.example.com/testorg/nginxIf the artifact exceeds the defined quota, and you set the Quota policy to Reject, the following error message is returned:
denied: Quota has been exceeded on namespaceIf the artifact exceeds the defined quota, and you set the Quota policy to Warning, no error message is returned, and the image is successfully pushed.
Notifications for both Reject and Warning policies are also returned on the Project Quay UI by clicking the bell icon.
Managing quota limits by using the API
When an organization is first created, it does not have an established quota. You can use the API to check, create, change, or delete quota limitations for an organization.
-
You have generated an OAuth access token.
Setting quota by using the API
Use the following procedure to set quota limitations by using the Project Quay API.
-
To set a quota for an organization, you can use the
POST /api/v1/organization/{orgname}/quotaendpoint:$ curl -X POST "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota" \ -H "Authorization: Bearer <access_token>" \ -H "Content-Type: application/json" \ -d '{ "limit_bytes": 10737418240, "limits": "10 Gi" }'Example output"Created" -
Use the
GET /api/v1/organization/{orgname}/quotacommand to see if your organization already has an established quota:$ curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' https://<quay-server.example.com>/api/v1/organization/<organization_name>/quota | jqExample output[{"id": 1, "limit_bytes": 10737418240, "limit": "10.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}] -
You can use the
PUT /api/v1/organization/{orgname}/quota/{quota_id}command to modify the existing quota limitation. For example:$ curl -X PUT "https://<quay-server.example.com>/api/v1/organization/<orgname>/quota/<quota_id>" \ -H "Authorization: Bearer <access_token>" \ -H "Content-Type: application/json" \ -d '{ "limit_bytes": <limit_in_bytes> }'Example output{"id": 1, "limit_bytes": 21474836480, "limit": "20.0 GiB", "default_config": false, "limits": [], "default_config_exists": false}
Viewing quota usage by using the API
Use the following procedure to view quota usage by using the Project Quay API.
-
To view the storage consumed,
GETdata from the /api/v1/repository endpoint:Sample command$ curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' 'https://example-registry-quay-quay-enterprise.apps.docs.gcp.quaydev.org/api/v1/repository?last_modified=true&namespace=testorg&popularity=true&public=true' | jqSample output{ "repositories": [ { "namespace": "testorg", "name": "ubuntu", "description": null, "is_public": false, "kind": "image", "state": "NORMAL", "quota_report": { "quota_bytes": 27959066, "configured_quota": 104857600 }, "last_modified": 1651225630, "popularity": 0, "is_starred": false } ] } -
To view the quota report for the repositories in the organization, use the /api/v1/repository endpoint:
Sample command$ curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' 'https://example-registry-quay-quay-enterprise.apps.docs.gcp.quaydev.org/api/v1/repository?last_modified=true&namespace=testorg&popularity=true&public=true'Sample output{ "repositories": [ { "namespace": "testorg", "name": "ubuntu", "description": null, "is_public": false, "kind": "image", "state": "NORMAL", "quota_report": { "quota_bytes": 27959066, "configured_quota": 104857600 }, "last_modified": 1651225630, "popularity": 0, "is_starred": false }, { "namespace": "testorg", "name": "nginx", "description": null, "is_public": false, "kind": "image", "state": "NORMAL", "quota_report": { "quota_bytes": 59231659, "configured_quota": 104857600 }, "last_modified": 1651229507, "popularity": 0, "is_starred": false } ] } -
To view the quota information in the organization details, use the /api/v1/organization/{orgname} endpoint:
Sample command$ curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' 'https://example-registry-quay-quay-enterprise.apps.docs.gcp.quaydev.org/api/v1/organization/testorg' | jqSample output{ "name": "testorg", ... "quotas": [ { "id": 1, "limit_bytes": 104857600, "limits": [] } ], "quota_report": { "quota_bytes": 87190725, "configured_quota": 104857600 } }
Setting reject and warning limits by using the API
You can set reject and warning limits by using the Project Quay API.
-
To set reject and warning limits,
POSTdata to the /api/v1/organization/{orgname}/quota/{quota_id}/limit endpoint. For example:$ curl -k -X POST -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' -d '{"type":"Reject","threshold_percent":80}' https://example-registry-quay-quay-enterprise.apps.docs.gcp.quaydev.org/api/v1/organization/testorg/quota/1/limit$ curl -k -X POST -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' -d '{"type":"Warning","threshold_percent":50}' https://example-registry-quay-quay-enterprise.apps.docs.gcp.quaydev.org/api/v1/organization/testorg/quota/1/limit
Viewing reject and warning limits by using the API
You can use the Project Quay API to view reject and warning limits.
-
View the reject and warning limits by using the /api/v1/organization/{orgname}/quota endpoint. For example:
$ curl -k -X GET -H "Authorization: Bearer <token>" -H 'Content-Type: application/json' https://example-registry-quay-quay-enterprise.apps.docs.gcp.quaydev.org/api/v1/organization/testorg/quota | jqExample output[ { "id": 1, "limit_bytes": 104857600, "default_config": false, "limits": [ { "id": 2, "type": "Warning", "limit_percent": 50 }, { "id": 1, "type": "Reject", "limit_percent": 80 } ], "default_config_exists": false } ]
Calculating the total registry size
Use the following procedure to queue a registry total calculation.
|
Note
|
This feature is done on-demand. Calculating a registry total is database intensive. Use with caution. |
-
You are logged in as a Project Quay superuser.
-
On the Project Quay UI, click your username → Super User Admin Panel.
-
In the navigation pane, click Manage Organizations.
-
Click Calculate → Ok.
-
After a few minutes, depending on the size of your registry, refresh the page. The Total Registry Size is now calculated.
Permanently deleting an image tag
In some cases, users might want to delete an image tag outside of the time machine window. Use the following procedure to manually delete an image tag permanently.
|
Important
|
The results of the following procedure cannot be undone. Use with caution. |
Permanently deleting an image tag using the Project Quay v2 UI
Use the following procedure to permanently delete an image tag using the Project Quay v2 UI.
-
You have set
FEATURE_UI_V2toTruein yourconfig.yamlfile.
-
Ensure that the
PERMANENTLY_DELETE_TAGSandRESET_CHILD_MANIFEST_EXPIRATIONparameters are set toTruein yourconfig.yamlfile. For example:PERMANENTLY_DELETE_TAGS: true RESET_CHILD_MANIFEST_EXPIRATION: true -
In the navigation pane, click Repositories.
-
Click the name of the repository, for example, quayadmin/busybox.
-
Check the box of the image tag that will be deleted, for example, test.
-
Click Actions → Permanently Delete.
ImportantThis action is permanent and cannot be undone.
Permanently deleting an image tag using the Project Quay legacy UI
Use the following procedure to permanently delete an image tag using the Project Quay legacy UI.
-
Ensure that the
PERMANENTLY_DELETE_TAGSandRESET_CHILD_MANIFEST_EXPIRATIONparameters are set toTruein yourconfig.yamlfile. For example:PERMANENTLY_DELETE_TAGS: true RESET_CHILD_MANIFEST_EXPIRATION: true -
On the Project Quay UI, click Repositories and the name of the repository that contains the image tag you will delete, for example, quayadmin/busybox.
-
In the navigation pane, click Tags.
-
Check the box of the name of the tag you want to delete, for example, test.
-
Click the Actions drop down menu and select Delete Tags → Delete Tag.
-
Click Tag History in the navigation pane.
-
On the name of the tag that was just deleted, for example,
test, click Delete test under the Permanently Delete category. For example:ImportantThis action is permanent and cannot be undone.
Project Quay auto-pruning overview
Project Quay administrators can set up multiple auto-pruning policies on organizations and repositories; administrators can also set up auto-pruning policies at the registry level so that they apply to all organizations, including all newly created organizations. This feature allows for image tags to be automatically deleted within an organization or a repository based on specified criteria, which allows Project Quay organization owners to stay below the storage quota by automatically pruning content.
Currently, two policies have been added:
-
Prune images by the number of tags. For this policy, when the actual number of tags exceeds the desired number of tags, the oldest tags are deleted by their creation date until the desired number of tags is achieved.
-
Prune image tags by creation date. For this policy, any tags with a creation date older than the given time span, for example, 10 days, are deleted.
After tags are automatically pruned, they go into the Project Quay time machine, or the amount of time, after a tag is deleted, that the tag is accessible before being garbage collected. The expiration time of an image tag is dependent on your organization’s settings. For more information, see Project Quay garbage collection.
Users can configure multiple policies per namespace or repository; this can be done through the Project Quay v2 UI. Policies can also be set by using the API endpoints through the command-line interface (CLI).
Prerequisites and limitations for auto-pruning and multiple policies
The following prerequisites and limitations apply to the auto-pruning feature:
-
Auto-pruning is not available when using the Project Quay legacy UI. You must use the v2 UI to create, view, or modify auto-pruning policies.
-
Auto-pruning is only supported in databases that support the
FOR UPDATE SKIP LOCKEDSQL command. -
Auto-pruning is unavailable on mirrored repositories and read-only repositories.
-
If you are configuring multiple auto-prune policies, rules are processed without particular order, and individual result sets are processed immediately before moving on to the next rule.
-
For example, if an image is already subject for garbage collection by one rule, it cannot be excluded from pruning by another rule.
-
-
If you have both an auto-pruning policy for an organization and a repository, the auto-pruning policies set at the organization level are executed first.
Regular expressions with auto-pruning
Project Quay administrators can leverage regular expressions, or regex, to match a subset of tags for both organization- and repository-level auto-pruning policies. This provides more granular auto-pruning policies to target only certain image tags for removal. Consider the following when using regular expressions with the auto-pruning feature:
-
Regular expressions are optional.
-
If a regular expression is not provided, the auto-pruner defaults to pruning all image tags in the organization or the repository. These are user-supplied and must be protected against ReDOS attacks.
-
Registry-wide policies do not currently support regular expressions. Only organization- and repository-level auto-pruning policies support regular expressions.
-
Regular expressions can be configured to prune images that either do, or do not, match the provided regex pattern.
Some of the following procedures provide example auto-pruning policies using regular expressions that you can use as a reference when creating an auto-prune policy.
Managing auto-pruning policies using the Project Quay UI
All auto-pruning policies, with the exception of a registry-wide auto pruning policy, are created using the Project Quay v2 UI or by using the API. This can be done after you have configured your Project Quay config.yaml file to enable the auto-pruning feature and the v2 UI.
Enabling image pull activity tracking
Project Quay administrators can enable image pull activity tracking, which provides clear visibility into how often and when image tags are pulled, giving users valuable insight into image usage and popularity across repositories. The following procedure shows you how to enable this feature.
-
In your Project Quay
config.yamlfile, setFEATURE_IMAGE_PULL_STATS: true. For example:# ... FEATURE_IMAGE_PULL_STATS: true REDIS_FLUSH_INTERVAL_SECONDS: 30 PULL_METRICS_REDIS: host: <redis_host> password: <redis_password> port: 6379 db: 1 # ...-
FEATURE_IMAGE_PULL_STATSenables image pull tracking activity. -
REDIS_FLUSH_INTERVAL_SECONDSdefines the time, in seconds, at which the Redis flush worker clears old data. Shorter intervals keep data fresher and help prevent Redis from bloating, while longer intervals reduce flush frequency. -
PULL_METRICS_REDISSpecifies the connection settings for the Redis database used to store image pull metrics.
-
-
Restart your Project Quay deployment.
-
Push an image to your registry by entering the following command. Following this step, you can use your browser to see the tagged image in your repository.
$ podman push <quay-server.example.com>/<organization>/<image>:<tag> -
Pull the image from your Project Quay registry by entering the following command:
$ podman pull <quay-server.example.com>/<organization>/<image>:<tag> -
On the Project Quay UI, navigate to Repositories, and then click the name of your repository.
-
Click Tags. The Last Pulled and Pull Count categories show you information about when the image was last pull, and how many time it has been pulled, respectively. For example:
Configuring the Project Quay auto-pruning feature
Use the following procedure to configure your Project Quay config.yaml file to enable the auto-pruning feature.
-
You have set
FEATURE_UI_V2toTruein yourconfig.yamlfile.
-
In your Project Quay
config.yamlfile, add, and set, theFEATURE_AUTO_PRUNEenvironment variable toTrue. For example:# ... FEATURE_AUTO_PRUNE: true # ...
Creating a registry-wide auto-pruning policy
Registry-wide auto-pruning policies can be configured on new and existing organizations. This feature saves Project Quay administrators time, effort, and storage by enforcing registry-wide rules.
Project Quay administrators must enable this feature by updating their config.yaml file through the inclusion of DEFAULT_NAMESPACE_AUTOPRUNE_POLICY configuration field, and one of number_of_tags or creation_date methods. Currently, this feature cannot be enabled by using the v2 UI or the API.
Use the following procedure to create an auto-prune policy for your Project Quay registry.
-
You have enabled the
FEATURE_AUTO_PRUNEfeature.
-
Update your
config.yamlfile to add theDEFAULT_NAMESPACE_AUTOPRUNE_POLICYconfiguration field:-
To set the policy method to remove the oldest tags by their creation date until the number of tags provided is left, use the
number_of_tagsmethod:# ... DEFAULT_NAMESPACE_AUTOPRUNE_POLICY: method: number_of_tags value: 2 (1) # ...-
In this scenario, two tags remain.
-
-
To set the policy method to remove tags with a creation date older than the provided time span, for example,
5d, use thecreation_datemethod:DEFAULT_NAMESPACE_AUTOPRUNE_POLICY: method: creation_date value: 5d
-
-
Restart your Project Quay deployment.
-
Optional. If you need to tag and push images to test this feature:
-
Tag four sample images that will be pushed to a Project Quay registry. For example:
$ podman tag docker.io/library/busybox <quay-server.example.com>/<quayadmin>/busybox:test$ podman tag docker.io/library/busybox <quay-server.example.com>/<quayadmin>/busybox:test2$ podman tag docker.io/library/busybox <quay-server.example.com>/<quayadmin>/busybox:test3$ podman tag docker.io/library/busybox <quay-server.example.com>/<quayadmin>/busybox:test4 -
Push the four sample images to the registry with auto-pruning enabled by entering the following commands:
$ podman push <quay-server.example.com>/quayadmin/busybox:test$ podman push <quay-server.example.com>/<quayadmin>/busybox:test2$ podman push <quay-server.example.com>/<quayadmin>/busybox:test3$ podman push <quay-server.example.com>/<quayadmin>/busybox:test4
-
-
Check that there are four tags in the registry that you pushed the images to.
-
By default, the auto-pruner worker at the registry level runs every 24 hours. After 24 hours, the two oldest image tags are removed, leaving the
test3andtest4tags if you followed these instructions. Check your Project Quay organization to ensure that the two oldest tags were removed.
Creating an auto-prune policy for an organization by using the Project Quay v2 UI
Use the following procedure to create an auto-prune policy for an organization using the Project Quay v2 UI.
-
You have enabled the
FEATURE_AUTO_PRUNEfeature. -
Your organization has image tags that have been pushed to it.
-
On the Project Quay v2 UI, click Organizations in the navigation pane.
-
Select the name of an organization that you will apply the auto-pruning feature to, for example,
test_organization. -
Click Settings.
-
Click Auto-Prune Policies. For example:
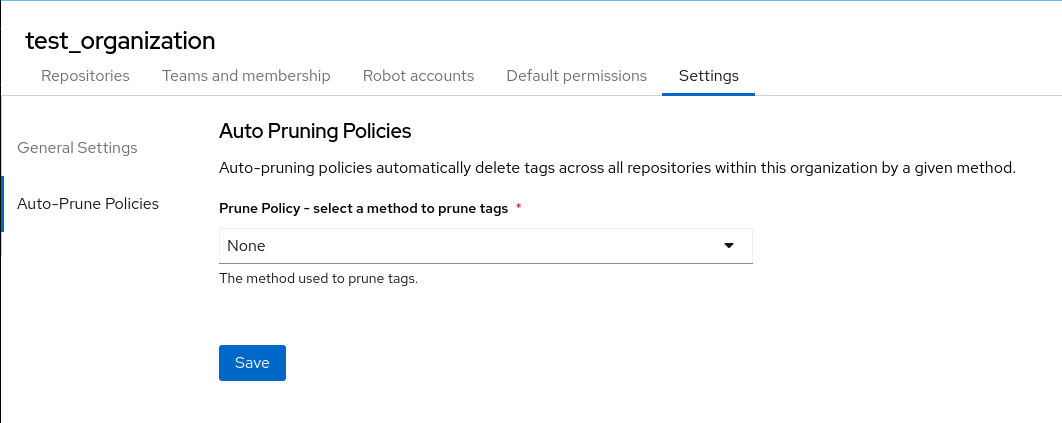
-
Click the drop down menu and select the desired policy, for example, By number of tags.
-
Select the desired number of tags to keep. By default, this is set at 20 tags. For this example, the number of tags to keep is set at 3.
-
Optional. With the introduction of regular expressions, you are provided the following options to fine-grain your auto-pruning policy:
-
Match: When selecting this option, the auto-pruner prunes all tags that match the given regex pattern.
-
Does not match: When selecting this option, the auto-pruner prunes all tags that do not match the regex pattern.
If you do not select an option, the auto-pruner defaults to pruning all image tags.
For this example, click the Tag pattern box and select match. In the regex box, enter a pattern to match tags against. For example, to automatically prune all
testtags, enter^test.*.
-
-
Optional. You can create a second auto-prune policy by clicking Add Policy and entering the required information.
-
Click Save. A notification that your auto-prune policy has been updated appears.
With this example, the organization is configured to keep the three latest tags that are named
^test.*.
-
Navigate to the Tags page of your Organization’s repository. After a few minutes, the auto-pruner worker removes tags that no longer fit within the established criteria. In this example, it removes the
busybox:testtag, and keeps thebusybox:test2,busybox:test3, andbusybox:test4tag.After tags are automatically pruned, they go into the Project Quay time machine, or the amount of time after a tag is deleted that the tag is accessible before being garbage collected. The expiration time of an image tag is dependent on your organization’s settings. For more information, see Project Quay garbage collection.
Creating an auto-prune policy for a namespace by using the Project Quay API
You can use Project Quay API endpoints to manage auto-pruning policies for an namespace.
-
You have created an OAuth access token.
-
You have logged into Project Quay.
-
Enter the following
POST /api/v1/organization/{orgname}/autoprunepolicy/command create a new policy that limits the number of tags allowed in an organization:$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags", "value": 10}' http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/Alternatively, you can can set tags to expire for a specified time after their creation date:
$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{ "method": "creation_date", "value": "7d"}' http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/Example output{"uuid": "73d64f05-d587-42d9-af6d-e726a4a80d6e"} -
Optional. You can add an additional policy to an organization and pass in the
tagPatternandtagPatternMatchesfields to prune only tags that match the given regex pattern. For example:$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ -H "Content-Type: application/json" \ -d '{ "method": "creation_date", "value": "7d", "tagPattern": "^v*", "tagPatternMatches": <true> (1) }' \ "https://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/"-
Setting
tagPatternMatchestoTruemakes it so that tags that match the given regex pattern will be pruned. In this example, tags that match^v*are pruned.Example output{"uuid": "ebf7448b-93c3-4f14-bf2f-25aa6857c7b0"}
-
-
You can update your organization’s auto-prune policy by using the
PUT /api/v1/organization/{orgname}/autoprunepolicy/{policy_uuid}command. For example:$ curl -X PUT -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{ "method": "creation_date", "value": "4d", "tagPattern": "^v*", "tagPatternMatches": true }' "<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/<uuid>"This command does not return output. Continue to the next step.
-
Check your auto-prune policy by entering the following command:
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/Example output{"policies": [{"uuid": "ebf7448b-93c3-4f14-bf2f-25aa6857c7b0", "method": "creation_date", "value": "4d", "tagPattern": "^v*", "tagPatternMatches": true}, {"uuid": "da4d0ad7-3c2d-4be8-af63-9c51f9a501bc", "method": "number_of_tags", "value": 10, "tagPattern": null, "tagPatternMatches": true}, {"uuid": "17b9fd96-1537-4462-a830-7f53b43f94c2", "method": "creation_date", "value": "7d", "tagPattern": "^v*", "tagPatternMatches": true}]} -
You can delete the auto-prune policy for your organization by entering the following command. Note that deleting the policy requires the UUID.
$ curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/organization/<organization_name>/autoprunepolicy/73d64f05-d587-42d9-af6d-e726a4a80d6e
Creating an auto-prune policy for a namespace for the current user by using the API
You can use Project Quay API endpoints to manage auto-pruning policies for your account.
|
Note
|
The use of |
-
You have created an OAuth access token.
-
You have logged into Project Quay.
-
Enter the following
POSTcommand create a new policy that limits the number of tags for the current user:$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags", "value": 10}' http://<quay-server.example.com>/api/v1/user/autoprunepolicy/Example output{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859"} -
Check your auto-prune policy by entering the following command:
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/Alternatively, you can include the UUID:
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/8c03f995-ca6f-4928-b98d-d75ed8c14859Example output{"policies": [{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859", "method": "number_of_tags", "value": 10}]} -
You can delete the auto-prune policy by entering the following command. Note that deleting the policy requires the UUID.
$ curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/user/autoprunepolicy/8c03f995-ca6f-4928-b98d-d75ed8c14859Example output{"uuid": "8c03f995-ca6f-4928-b98d-d75ed8c14859"}
Creating an auto-prune policy for a repository using the Project Quay v2 UI
Use the following procedure to create an auto-prune policy for a repository using the Project Quay v2 UI.
-
You have enabled the
FEATURE_AUTO_PRUNEfeature. -
You have pushed image tags to your repository.
-
On the Project Quay v2 UI, click Repository in the navigation pane.
-
Select the name of an organization that you will apply the auto-pruning feature to, for example,
<organization_name>/<repository_name>. -
Click Settings.
-
Click Repository Auto-Prune Policies.
-
Click the drop down menu and select the desired policy, for example, By age of tags.
-
Set a time, for example,
5and an interval, for exampleminutesto delete tags older than the specified time frame. For this example, tags older than 5 minutes are marked for deletion. -
Optional. With the introduction of regular expressions, you are provided the following options to fine-grain your auto-pruning policy:
-
Match: When selecting this option, the auto-pruner prunes all tags that match the given regex pattern.
-
Does not match: When selecting this option, the auto-pruner prunes all tags that do not match the regex pattern.
If you do not select an option, the auto-pruner defaults to pruning all image tags.
For this example, click the Tag pattern box and select Does not match. In the regex box, enter a pattern to match tags against. For example, to automatically prune all tags that do not match the
testtag, enter^test.*.
-
-
Optional. You can create a second auto-prune policy by clicking Add Policy and entering the required information.
-
Click Save. A notification that your auto-prune policy has been updated appears.
-
Navigate to the Tags page of your Organization’s repository. With this example, Tags that are older than 5 minutes that do not match the
^test.*regex tag are automatically pruned when the pruner runs.After tags are automatically pruned, they go into the Project Quay time machine, or the amount of time after a tag is deleted that the tag is accessible before being garbage collected. The expiration time of an image tag is dependent on your organization’s settings. For more information, see Project Quay garbage collection.
Creating an auto-prune policy for a repository using the Project Quay API
You can use Project Quay API endpoints to manage auto-pruning policies for an repository.
-
You have created an OAuth access token.
-
You have logged into Project Quay.
-
Enter the following
POST /api/v1/repository/{repository}/autoprunepolicy/command create a new policy that limits the number of tags allowed in an organization:$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags","value": 2}' http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/Alternatively, you can can set tags to expire for a specified time after their creation date:
$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "creation_date", "value": "7d"}' http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/Example output{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7"} -
Optional. You can add an additional policy and pass in the
tagPatternandtagPatternMatchesfields to prune only tags that match the given regex pattern. For example:$ curl -X POST \ -H "Authorization: Bearer <access_token>" \ -H "Content-Type: application/json" \ -d '{ "method": "<creation_date>", "value": "<7d>", "tagPattern": "<^test.>*", "tagPatternMatches": <false> (1) }' \ "https://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/"-
Setting
tagPatternMatchestoFalsemakes it so that tags that all tags that do not match the given regex pattern are pruned. In this example, all tags but^test.are pruned.Example output{"uuid": "b53d8d3f-2e73-40e7-96ff-736d372cd5ef"}
-
-
You can update your policy for the repository by using the
PUT /api/v1/repository/{repository}/autoprunepolicy/{policy_uuid}command and passing in the UUID. For example:$ curl -X PUT \ -H "Authorization: Bearer <bearer_token>" \ -H "Content-Type: application/json" \ -d '{ "method": "number_of_tags", "value": "5", "tagPattern": "^test.*", "tagPatternMatches": true }' \ "https://quay-server.example.com/api/v1/repository/<namespace>/<repo_name>/autoprunepolicy/<uuid>"This command does not return output. Continue to the next step to check your auto-prune policy.
-
Check your auto-prune policy by entering the following command:
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/Alternatively, you can include the UUID:
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7Example output{"policies": [{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7", "method": "number_of_tags", "value": 10}]} -
You can delete the auto-prune policy by entering the following command. Note that deleting the policy requires the UUID.
$ curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<organization_name>/<repository_name>/autoprunepolicy/ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7Example output{"uuid": "ce2bdcc0-ced2-4a1a-ac36-78a9c1bed8c7"}
Creating an auto-prune policy on a repository for a user with the API
You can use Project Quay API endpoints to manage auto-pruning policies on a repository for user accounts that are not your own, so long as you have admin privileges on the repository.
-
You have created an OAuth access token.
-
You have logged into Project Quay.
-
You have
adminprivileges on the repository that you are creating the policy for.
-
Enter the following
POST /api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/command create a new policy that limits the number of tags for the user:$ curl -X POST -H "Authorization: Bearer <access_token>" -H "Content-Type: application/json" -d '{"method": "number_of_tags","value": 2}' https://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/Example output{"uuid": "7726f79c-cbc7-490e-98dd-becdc6fefce7"} -
Optional. You can add an additional policy for the current user and pass in the
tagPatternandtagPatternMatchesfields to prune only tags that match the given regex pattern. For example:$ curl -X POST \ -H "Authorization: Bearer <bearer_token>" \ -H "Content-Type: application/json" \ -d '{ "method": "creation_date", "value": "7d", "tagPattern": "^v*", "tagPatternMatches": true }' \ "http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/"Example output{"uuid": "b3797bcd-de72-4b71-9b1e-726dabc971be"} -
You can update your policy for the current user by using the
PUT /api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/<policy_uuid>command. For example:$ curl -X PUT -H "Authorization: Bearer <bearer_token>" -H "Content-Type: application/json" -d '{ "method": "creation_date", "value": "4d", "tagPattern": "^test.", "tagPatternMatches": true }' "https://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/<policy_uuid>"Updating a policy does not return output in the CLI.
-
Check your auto-prune policy by entering the following command:
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/Alternatively, you can include the UUID:
$ curl -X GET -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/7726f79c-cbc7-490e-98dd-becdc6fefce7Example output{"uuid": "81ee77ec-496a-4a0a-9241-eca49437d15b", "method": "creation_date", "value": "7d", "tagPattern": "^v*", "tagPatternMatches": true} -
You can delete the auto-prune policy by entering the following command. Note that deleting the policy requires the UUID.
$ curl -X DELETE -H "Authorization: Bearer <access_token>" http://<quay-server.example.com>/api/v1/repository/<user_account>/<user_repository>/autoprunepolicy/<policy_uuid>Example output{"uuid": "7726f79c-cbc7-490e-98dd-becdc6fefce7"}
Geo-replication
Geo-replication lets multiple geographically distributed Project Quay deployments work as a single registry from the client perspective. This improves push and pull performance in globally distributed setups and provides transparent failover and redirect for clients.
Geo-replication is supported on standalone and Operator-based deployments.
Geo-replication features
Geo-replication features optimize image push and pull operations by routing pushes to the nearest storage backend and replicating data in the background to other locations. Pulls automatically use the closest available storage engine to maximize performance, with fallback to the source storage if replication is incomplete.
The following are the key features of geo-replication:
-
When geo-replication is configured, container image pushes are written to the preferred storage engine for that Project Quay instance. This is typically the nearest storage backend within the region.
-
After the initial push, image data is replicated in the background to other storage engines.
-
The list of replication locations is configurable and those can be different storage backends.
-
An image pull always uses the closest available storage engine to maximize pull performance.
-
If replication has not been completed yet, the pull uses the source storage backend instead.
Geo-replication requirements and constraints
To run geo-replication reliably in Project Quay, you must meet strict requirements for shared object storage, networking, load balancing, and external health monitoring. Geo-replication does not provide automatic failover, database replication, or storage awareness, so you must design and manage these behaviors outside of Project Quay.
The following are the requirements and constraints for geo-replication:
-
In geo-replicated setups, Project Quay requires that all regions are able to read and write to all other region’s object storage. Object storage must be geographically accessible by all other regions.
-
In case of an object storage system failure of one geo-replicating site, that site’s Project Quay deployment must be shut down so that clients are redirected to the remaining site with intact storage systems by a global load balancer. Otherwise, clients will experience pull and push failures.
-
Project Quay has no internal awareness of the health or availability of the connected object storage system. Users must configure a global load balancer (LB) to monitor the health of your distributed system and to route traffic to different sites based on their storage status.
-
To check the status of your geo-replication deployment, you must use the
/health/endtoendcheckpoint, which is used for global health monitoring. You must configure the redirect manually using the/health/endtoendendpoint. The/health/instanceend point only checks local instance health. -
If the object storage system of one site becomes unavailable, there will be no automatic redirect to the remaining storage system, or systems, of the remaining site, or sites.
-
Geo-replication is asynchronous. The permanent loss of a site incurs the loss of the data that has been saved in that sites' object storage system but has not yet been replicated to the remaining sites at the time of failure.
-
A single database, and therefore all metadata and Project Quay configuration, is shared across all regions.
Geo-replication does not replicate the database. In the event of an outage, Project Quay with geo-replication enabled will not failover to another database.
-
A single Redis cache is shared across the entire Project Quay setup and needs to be accessible by all Project Quay pods.
-
The exact same configuration should be used across all regions, with exception of the storage backend, which can be configured explicitly using the
QUAY_DISTRIBUTED_STORAGE_PREFERENCEenvironment variable. -
Geo-replication requires object storage in each region. It does not work with local storage.
-
Each region must be able to access every storage engine in each region, which requires a network path.
-
Alternatively, the storage proxy option can be used.
-
The entire storage backend, for example, all blobs, is replicated. Repository mirroring, by contrast, can be limited to a repository, or an image.
-
All Project Quay instances must share the same entrypoint, typically through a load balancer.
-
All Project Quay instances must have the same set of superusers, as they are defined inside the common configuration file.
-
In geo-replication environments, your Clair configuration can be set to
unmanaged. An unmanaged Clair database allows the Project Quay Operator to work in a geo-replicated environment where multiple instances of the Operator must communicate with the same database. For more information, see Advanced Clair configuration.If you keep your Clair configuration
managed, you must retrieve the configuration file for the deployed Clair instance that is deployed by the Operator. For more information, see Retrieving and decoding the Clair configuration secret for Clair deployments on OpenShift Container Platform. -
Geo-Replication requires SSL/TLS certificates and keys. For more information, see * Geo-Replication requires SSL/TLS certificates and keys. For more information, see Proof of concept deployment using SSL/TLS certificates. .
If the above requirements cannot be met, you should instead use two or more distinct Project Quay deployments and take advantage of repository mirroring functions.
Enabling storage replication for standalone Project Quay
Use the following procedure to enable storage replication on Project Quay.
-
Update your
config.yamlfile to include the storage engines to which data will be replicated. You must list all storage engines to be used:# ... FEATURE_STORAGE_REPLICATION: true # ... DISTRIBUTED_STORAGE_CONFIG: usstorage: - RHOCSStorage - access_key: <access_key> bucket_name: <example_bucket> hostname: my.noobaa.hostname is_secure: false port: "443" secret_key: <secret_key> storage_path: /datastorage/registry eustorage: - S3Storage - host: s3.amazon.com port: "443" s3_access_key: <access_key> s3_bucket: <example bucket> s3_secret_key: <secret_key> storage_path: /datastorage/registry DISTRIBUTED_STORAGE_DEFAULT_LOCATIONS: [] DISTRIBUTED_STORAGE_PREFERENCE: - usstorage - eustorage # ... -
Optional. If complete replication of all images to all storage engines is required, you can replicate images to the storage engine by manually setting the
DISTRIBUTED_STORAGE_DEFAULT_LOCATIONSfield. This ensures that all images are replicated to that storage engine. For example:# ... DISTRIBUTED_STORAGE_DEFAULT_LOCATIONS: - usstorage - eustorage # ...NoteTo enable per-namespace replication, contact Project Quay support.
-
After adding storage and enabling Replicate to storage engine by default for geo-replication, you must sync existing image data across all storage. To do this, you must execute into the container by running the following command:
$ podman exec -it <container_id> -
To sync the content after adding new storage, enter the following commands:
# scl enable python27 bash# python -m util.backfillreplicationNoteThis is a one time operation to sync content after adding new storage.
Run Project Quay with storage preferences
-
Copy the config.yaml to all machines running Project Quay
-
For each machine in each region, add a
QUAY_DISTRIBUTED_STORAGE_PREFERENCEenvironment variable with the preferred storage engine for the region in which the machine is running.For example, for a machine running in Europe with the config directory on the host available from
$QUAY/config:$ sudo podman run -d --rm -p 80:8080 -p 443:8443 \ --name=quay \ -v $QUAY/config:/conf/stack:Z \ -e QUAY_DISTRIBUTED_STORAGE_PREFERENCE=europestorage \ quay.io/projectquay/quay:v3.17.0
NoteThe value of the environment variable specified must match the name of a Location ID as defined in the config panel.
-
Restart all Project Quay containers
Removing a geo-replicated site from your standalone Project Quay deployment
By using the following procedure, Project Quay administrators can remove sites in a geo-replicated setup.
-
You have configured Project Quay geo-replication with at least two sites, for example,
usstorageandeustorage. -
Each site has its own Organization, Repository, and image tags.
-
Sync the blobs between all of your defined sites by running the following command:
$ python -m util.backfillreplicationWarningPrior to removing storage engines from your Project Quay
config.yamlfile, you must ensure that all blobs are synced between all defined sites. Complete this step before proceeding. -
In your Project Quay
config.yamlfile for siteusstorage, remove theDISTRIBUTED_STORAGE_CONFIGentry for theeustoragesite. -
Enter the following command to obtain a list of running containers:
$ podman psExample outputCONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 92c5321cde38 registry.redhat.io/rhel8/redis-5:1 run-redis 11 days ago Up 11 days ago 0.0.0.0:6379->6379/tcp redis 4e6d1ecd3811 registry.redhat.io/rhel8/postgresql-13:1-109 run-postgresql 33 seconds ago Up 34 seconds ago 0.0.0.0:5432->5432/tcp postgresql-quay d2eadac74fda registry-proxy.engineering.redhat.com/rh-osbs/quay-quay-rhel8:v3.9.0-131 registry 4 seconds ago Up 4 seconds ago 0.0.0.0:80->8080/tcp, 0.0.0.0:443->8443/tcp quay -
Enter the following command to execute a shell inside of the PostgreSQL container:
$ podman exec -it postgresql-quay -- /bin/bash -
Enter psql by running the following command:
bash-4.4$ psql -
Enter the following command to reveal a list of sites in your geo-replicated deployment:
quay=# select * from imagestoragelocation;Example outputid | name ----+------------------- 1 | usstorage 2 | eustorage -
Enter the following command to exit the postgres CLI to re-enter bash-4.4:
\q -
Enter the following command to permanently remove the
eustoragesite:ImportantThe following action cannot be undone. Use with caution.
bash-4.4$ python -m util.removelocation eustorageExample outputWARNING: This is a destructive operation. Are you sure you want to remove eustorage from your storage locations? [y/n] y Deleted placement 30 Deleted placement 31 Deleted placement 32 Deleted placement 33 Deleted location eustorage
Preparing your OpenShift Container Platform environment for geo-replication
To prepare your OpenShift Container Platform environment for geo-replication, you must deploy shared PostgreSQL and Redis instances, create object storage backends for each cluster, and configure a load balancer. This sets up the infrastructure needed for multiple Project Quay deployments to work as a single registry.
-
Deploy a PostgreSQL instance for Project Quay.
-
Login to the database by entering the following command:
psql -U <username> -h <hostname> -p <port> -d <database_name> -
Create a database for Project Quay named
quay. For example:CREATE DATABASE quay; -
Enable pg_trm extension inside the database
\c quay; CREATE EXTENSION IF NOT EXISTS pg_trgm; -
Deploy a Redis instance:
Note-
Deploying a Redis instance might be unnecessary if your cloud provider has its own service.
-
Deploying a Redis instance is required if you are leveraging Builders.
-
Deploy a VM for Redis
-
Verify that it is accessible from the clusters where Project Quay is running
-
Port 6379/TCP must be open
-
Run Redis inside the instance
sudo dnf install -y podman podman run -d --name redis -p 6379:6379 redis
-
-
Create two object storage backends, one for each cluster. Ideally, one object storage bucket will be close to the first, or primary, cluster, and the other will run closer to the second, or secondary, cluster.
-
Deploy the clusters with the same config bundle, using environment variable overrides to select the appropriate storage backend for an individual cluster.
-
Configure a load balancer to provide a single entry point to the clusters.
Removing a geo-replicated site from your Red Hat Quay on OpenShift Container Platform deployment
To remove a geo-replicated site from your Red Hat Quay on OpenShift Container Platform deployment, you must sync all blobs between sites, remove the storage configuration entry, and use the removelocation utility to permanently delete the site. This action cannot be undone, so ensure that all data is synchronized before proceeding.
-
You are logged into OpenShift Container Platform.
-
You have configured Project Quay geo-replication with at least two sites, for example,
usstorageandeustorage. -
Each site has its own Organization, Repository, and image tags.
-
Sync the blobs between all of your defined sites by running the following command:
$ python -m util.backfillreplicationWarningPrior to removing storage engines from your Project Quay
config.yamlfile, you must ensure that all blobs are synced between all defined sites.When running this command, replication jobs are created which are picked up by the replication worker. If there are blobs that need replicated, the script returns UUIDs of blobs that will be replicated. If you run this command multiple times, and the output from the return script is empty, it does not mean that the replication process is done; it means that there are no more blobs to be queued for replication. Customers should use appropriate judgement before proceeding, as the allotted time replication takes depends on the number of blobs detected.
Alternatively, you could use a third party cloud tool, such as Microsoft Azure, to check the synchronization status.
This step must be completed before proceeding.
-
In your Project Quay
config.yamlfile for siteusstorage, remove theDISTRIBUTED_STORAGE_CONFIGentry for theeustoragesite. -
Identify your Project Quay application pods by entering the following command:
$ oc get pod -n <quay_namespace>Example outputquay390usstorage-quay-app-5779ddc886-2drh2 quay390eustorage-quay-app-66969cd859-n2ssm -
Open an interactive shell session in the
usstoragepod by entering the following command:$ oc rsh quay390usstorage-quay-app-5779ddc886-2drh2 -
Permanently remove the
eustoragesite by entering the following command:ImportantThe following action cannot be undone. Use with caution.
sh-4.4$ python -m util.removelocation eustorageExample outputWARNING: This is a destructive operation. Are you sure you want to remove eustorage from your storage locations? [y/n] y Deleted placement 30 Deleted placement 31 Deleted placement 32 Deleted placement 33 Deleted location eustorage
Mixed storage for geo-replication
Geo-replication supports using different storage backends, such as AWS S3 in public cloud and Ceph on-premise, for replication targets. You must grant access to all storage backends from all Project Quay pods and cluster nodes, so use a VPN or token pair with bucket-specific access to meet security requirements.
Because geo-replication supports multiple replication targets, it is recommended to use a VPN or token pair with bucket-specific access to meet security requirements. This results in the public cloud instance of Project Quay having access to on-premise storage, but the network is encrypted, protected, and uses ACLs, thereby meeting security requirements. If you cannot implement these security measures, it might be preferable to deploy two distinct Project Quay registries and to use repository mirroring as an alternative to geo-replication.
Backing up and restoring Project Quay on a standalone deployment
Use the content within this section to back up and restore Project Quay in standalone deployments.
Optional: Enabling read-only mode for Project Quay
Enabling read-only mode for your Project Quay deployment allows you to manage the registry’s operations. Project Quay administrators can enable read-only mode to restrict write access to the registry, which helps ensure data integrity, mitigate risks during maintenance windows, and provide a safeguard against unintended modifications to registry data. It also helps to ensure that your Project Quay registry remains online and available to serve images to users.
|
Note
|
In some cases, a read-only option for Project Quay is not possible since it requires inserting a service key and other manual configuration changes. As an alternative to read-only mode, Project Quay administrators might consider enabling the This field might be useful in some situations such as when Project Quay administrators want to calculate their registry’s quota and disable image pushing until after calculation has completed. With this method, administrators can avoid putting putting the whole registry in For information about enabling this configuration field, see Miscellaneous configuration fields. |
-
If you are using Red Hat Enterprise Linux (RHEL) 7.x:
-
You have enabled the Red Hat Software Collections List (RHSCL).
-
You have installed Python 3.6.
-
You have downloaded the
virtualenvpackage. -
You have installed the
gitCLI.
-
-
If you are using Red Hat Enterprise Linux (RHEL) 8:
-
You have installed Python 3 on your machine.
-
You have downloaded the
python3-virtualenvpackage. -
You have installed the
gitCLI.
-
-
You have cloned the
https://github.com/quay/quay.gitrepository.
Creating service keys for standalone Project Quay
Project Quay uses service keys to communicate with various components. These keys are used to sign completed requests, such as requesting to scan images, login, storage access, and so on.
-
If your Project Quay registry is readily available, you can generate service keys inside of the
Quayregistry container.-
Enter the following command to generate a key pair inside of the
Quaycontainer:$ podman exec quay python3 tools/generatekeypair.py quay-readonly
-
-
If your Project Quay is not readily available, you must generate your service keys inside of a virtual environment.
-
Change into the directory of your Project Quay deployment and create a virtual environment inside of that directory:
$ cd <$QUAY>/quay && virtualenv -v venv -
Activate the virtual environment by entering the following command:
$ source venv/bin/activate -
Optional. Install the
pipCLI tool if you do not have it installed:$ venv/bin/pip install --upgrade pip -
In your Project Quay directory, create a
requirements-generatekeys.txtfile with the following content:$ cat << EOF > requirements-generatekeys.txt cryptography==3.4.7 pycparser==2.19 pycryptodome==3.9.4 pycryptodomex==3.9.4 pyjwkest==1.4.2 PyJWT==1.7.1 Authlib==1.0.0a2 EOF -
Enter the following command to install the Python dependencies defined in the
requirements-generatekeys.txtfile:$ venv/bin/pip install -r requirements-generatekeys.txt -
Enter the following command to create the necessary service keys:
$ PYTHONPATH=. venv/bin/python /<path_to_cloned_repo>/tools/generatekeypair.py quay-readonlyExample output
Writing public key to quay-readonly.jwk Writing key ID to quay-readonly.kid Writing private key to quay-readonly.pem -
Enter the following command to deactivate the virtual environment:
$ deactivate
-
Adding keys to the PostgreSQL database
Use the following procedure to add your service keys to the PostgreSQL database.
-
You have created the service keys.
-
Enter the following command to enter your Project Quay database environment:
$ podman exec -it postgresql-quay psql -U postgres -d quay -
Display the approval types and associated notes of the
servicekeyapprovalby entering the following command:quay=# select * from servicekeyapproval;Example output
id | approver_id | approval_type | approved_date | notes ----+-------------+----------------------------------+----------------------------+------- 1 | | ServiceKeyApprovalType.AUTOMATIC | 2024-05-07 03:47:48.181347 | 2 | | ServiceKeyApprovalType.AUTOMATIC | 2024-05-07 03:47:55.808087 | 3 | | ServiceKeyApprovalType.AUTOMATIC | 2024-05-07 03:49:04.27095 | 4 | | ServiceKeyApprovalType.AUTOMATIC | 2024-05-07 03:49:05.46235 | 5 | 1 | ServiceKeyApprovalType.SUPERUSER | 2024-05-07 04:05:10.296796 | ... -
Add the service key to your Project Quay database by entering the following query:
quay=# INSERT INTO servicekey (name, service, metadata, kid, jwk, created_date, expiration_date) VALUES ('quay-readonly', 'quay', '{}', '{<contents_of_.kid_file>}', '{<contents_of_.jwk_file>}', '{<created_date_of_read-only>}', '{<expiration_date_of_read-only>}');Example output
INSERT 0 1 -
Next, add the key approval with the following query:
quay=# INSERT INTO servicekeyapproval ('approval_type', 'approved_date', 'notes') VALUES ("ServiceKeyApprovalType.SUPERUSER", "CURRENT_DATE", {include_notes_here_on_why_this_is_being_added});Example output
INSERT 0 1 -
Set the
approval_idfield on the created service key row to theidfield from the created service key approval. You can use the followingSELECTstatements to get the necessary IDs:UPDATE servicekey SET approval_id = (SELECT id FROM servicekeyapproval WHERE approval_type = 'ServiceKeyApprovalType.SUPERUSER') WHERE name = 'quay-readonly';UPDATE 1
Configuring read-only mode for standalone Project Quay
After the service keys have been created and added to your PostgreSQL database, you must restart the Quay container on your standalone deployment.
-
You have created the service keys and added them to your PostgreSQL database.
-
Shutdown all Project Quay instances on all virtual machines. For example:
$ podman stop <quay_container_name_on_virtual_machine_a>$ podman stop <quay_container_name_on_virtual_machine_b> -
Enter the following command to copy the contents of the
quay-readonly.kidfile and thequay-readonly.pemfile to the directory that holds your Project Quay configuration bundle:$ cp quay-readonly.kid quay-readonly.pem $Quay/config -
Enter the following command to set file permissions on all files in your configuration bundle folder:
$ setfacl -m user:1001:rw $Quay/config/* -
Modify your Project Quay
config.yamlfile and add the following information:# ... REGISTRY_STATE: readonly INSTANCE_SERVICE_KEY_KID_LOCATION: 'conf/stack/quay-readonly.kid' INSTANCE_SERVICE_KEY_LOCATION: 'conf/stack/quay-readonly.pem' # ... -
Distribute the new configuration bundle to all Project Quay instances.
-
Start Project Quay by entering the following command:
$ podman run -d --rm -p 80:8080 -p 443:8443 \ --name=quay-main-app \ -v $QUAY/config:/conf/stack:Z \ -v $QUAY/storage:/datastorage:Z \ {productrepo}/{quayimage}:{productminv} -
After starting Project Quay, a banner inside in your instance informs users that Project Quay is running in read-only mode. Pushes should be rejected and a 405 error should be logged. You can test this by running the following command:
$ podman push <quay-server.example.com>/quayadmin/busybox:testExample output
613be09ab3c0: Preparing denied: System is currently read-only. Pulls will succeed but all write operations are currently suspended.With your Project Quay deployment on read-only mode, you can safely manage your registry’s operations and perform such actions as backup and restore.
-
Optional. After you are finished with read-only mode, you can return to normal operations by removing the following information from your
config.yamlfile. Then, restart your Project Quay deployment:# ... REGISTRY_STATE: readonly INSTANCE_SERVICE_KEY_KID_LOCATION: 'conf/stack/quay-readonly.kid' INSTANCE_SERVICE_KEY_LOCATION: 'conf/stack/quay-readonly.pem' # ...$ podman restart <container_id>
Updating read-only expiration time
The Project Quay read-only key has an expiration date, and when that date passes the key is deactivated. Before the key expires, its expiration time can be updated in the database. To update the key, connect your Project Quay production database using the methods described earlier and issue the following query:
quay=# UPDATE servicekey SET expiration_date = 'new-date' WHERE id = servicekey_id;The list of service key IDs can be obtained by running the following query:
SELECT id, name, expiration_date FROM servicekey;Backing up Project Quay on standalone deployments
This procedure describes how to create a backup of Project Quay on standalone deployments.
-
Create a temporary backup directory, for example,
quay-backup:$ mkdir /tmp/quay-backup -
The following example command denotes the local directory that the Project Quay was started in, for example,
/opt/quay-install:$ podman run --name quay-app \ -v /opt/quay-install/config:/conf/stack:Z \ -v /opt/quay-install/storage:/datastorage:Z \ quay.io/projectquay/quay:v3.17.0
Change into the directory that bind-mounts to
/conf/stackinside of the container, for example,/opt/quay-install, by running the following command:$ cd /opt/quay-install -
Compress the contents of your Project Quay deployment into an archive in the
quay-backupdirectory by entering the following command:$ tar cvf /tmp/quay-backup/quay-backup.tar.gz *Example output:
config.yaml config.yaml.bak extra_ca_certs/ extra_ca_certs/ca.crt ssl.cert ssl.key -
Back up the Quay container service by entering the following command:
$ podman inspect quay-app | jq -r '.[0].Config.CreateCommand | .[]' | paste -s -d ' ' - /usr/bin/podman run --name quay-app \ -v /opt/quay-install/config:/conf/stack:Z \ -v /opt/quay-install/storage:/datastorage:Z \ quay.io/projectquay/quay:v3.17.0
-
Redirect the contents of your
conf/stack/config.yamlfile to your temporaryquay-config.yamlfile by entering the following command:$ podman exec -it quay cat /conf/stack/config.yaml > /tmp/quay-backup/quay-config.yaml -
Obtain the
DB_URIlocated in your temporaryquay-config.yamlby entering the following command:$ grep DB_URI /tmp/quay-backup/quay-config.yamlExample output:
$ postgresql://<username>:test123@172.24.10.50/quay
-
Extract the PostgreSQL contents to your temporary backup directory in a backup .sql file by entering the following command:
$ pg_dump -h 172.24.10.50 -p 5432 -d quay -U <username> -W -O > /tmp/quay-backup/quay-backup.sql -
Print the contents of your
DISTRIBUTED_STORAGE_CONFIGby entering the following command:DISTRIBUTED_STORAGE_CONFIG: default: - S3Storage - s3_bucket: <bucket_name> storage_path: /registry s3_access_key: <s3_access_key> s3_secret_key: <s3_secret_key> host: <host_name> s3_region: <region> -
Export the
AWS_ACCESS_KEY_IDby using theaccess_keycredential obtained in Step 7:$ export AWS_ACCESS_KEY_ID=<access_key> -
Export the
AWS_SECRET_ACCESS_KEYby using thesecret_keyobtained in Step 7:$ export AWS_SECRET_ACCESS_KEY=<secret_key> -
Sync the
quaybucket to the/tmp/quay-backup/blob-backup/directory from thehostnameof yourDISTRIBUTED_STORAGE_CONFIG:$ aws s3 sync s3://<bucket_name> /tmp/quay-backup/blob-backup/ --source-region us-east-2Example output:
download: s3://<user_name>/registry/sha256/9c/9c3181779a868e09698b567a3c42f3744584ddb1398efe2c4ba569a99b823f7a to registry/sha256/9c/9c3181779a868e09698b567a3c42f3744584ddb1398efe2c4ba569a99b823f7a download: s3://<user_name>/registry/sha256/e9/e9c5463f15f0fd62df3898b36ace8d15386a6813ffb470f332698ecb34af5b0d to registry/sha256/e9/e9c5463f15f0fd62df3898b36ace8d15386a6813ffb470f332698ecb34af5b0d
It is recommended that you delete the quay-config.yaml file after syncing the quay bucket because it contains sensitive information. The quay-config.yaml file will not be lost because it is backed up in the quay-backup.tar.gz file.
Restoring Project Quay on standalone deployments
This procedure describes how to restore Project Quay on standalone deployments.
-
You have backed up your Project Quay deployment.
-
Create a new directory that will bind-mount to
/conf/stackinside of the Project Quay container:$ mkdir /opt/new-quay-install -
Copy the contents of your temporary backup directory created in Backing up Project Quay on standalone deployments to the
new-quay-install1directory created in Step 1:$ cp /tmp/quay-backup/quay-backup.tar.gz /opt/new-quay-install/ -
Change into the
new-quay-installdirectory by entering the following command:$ cd /opt/new-quay-install/ -
Extract the contents of your Project Quay directory:
$ tar xvf /tmp/quay-backup/quay-backup.tar.gz *Example output:
config.yaml config.yaml.bak extra_ca_certs/ extra_ca_certs/ca.crt ssl.cert ssl.key
-
Recall the
DB_URIfrom your backed-upconfig.yamlfile by entering the following command:$ grep DB_URI config.yamlExample output:
postgresql://<username>:test123@172.24.10.50/quay -
Run the following command to enter the PostgreSQL database server:
$ sudo postgres -
Enter psql and create a new database in 172.24.10.50 to restore the quay databases, for example,
example_restore_registry_quay_database, by entering the following command:$ psql "host=172.24.10.50 port=5432 dbname=postgres user=<username> password=test123" postgres=> CREATE DATABASE example_restore_registry_quay_database;Example output:
CREATE DATABASE
-
Connect to the database by running the following command:
postgres=# \c "example-restore-registry-quay-database";Example output:
You are now connected to database "example-restore-registry-quay-database" as user "postgres". -
Create a
pg_trmgextension of your Quay database by running the following command:example_restore_registry_quay_database=> CREATE EXTENSION IF NOT EXISTS pg_trgm;Example output:
CREATE EXTENSION -
Exit the postgres CLI by entering the following command:
\q -
Import the database backup to your new database by running the following command:
$ psql "host=172.24.10.50 port=5432 dbname=example_restore_registry_quay_database user=<username> password=test123" -W < /tmp/quay-backup/quay-backup.sqlExample output:
SET SET SET SET SET
Update the value of
DB_URIin yourconfig.yamlfrompostgresql://<username>:test123@172.24.10.50/quaytopostgresql://<username>:test123@172.24.10.50/example-restore-registry-quay-databasebefore restarting the Project Quay deployment.NoteThe DB_URI format is
DB_URI postgresql://<login_user_name>:<login_user_password>@<postgresql_host>/<quay_database>. If you are moving from one PostgreSQL server to another PostgreSQL server, update the value of<login_user_name>,<login_user_password>and<postgresql_host>at the same time. -
In the
/opt/new-quay-installdirectory, print the contents of yourDISTRIBUTED_STORAGE_CONFIGbundle:$ cat config.yaml | grep DISTRIBUTED_STORAGE_CONFIG -A10Example output:
DISTRIBUTED_STORAGE_CONFIG: default: DISTRIBUTED_STORAGE_CONFIG: default: - S3Storage - s3_bucket: <bucket_name> storage_path: /registry s3_access_key: <s3_access_key> s3_region: <region> s3_secret_key: <s3_secret_key> host: <host_name>NoteYour
DISTRIBUTED_STORAGE_CONFIGin/opt/new-quay-installmust be updated before restarting your Project Quay deployment. -
Export the
AWS_ACCESS_KEY_IDby using theaccess_keycredential obtained in Step 13:$ export AWS_ACCESS_KEY_ID=<access_key> -
Export the
AWS_SECRET_ACCESS_KEYby using thesecret_keyobtained in Step 13:$ export AWS_SECRET_ACCESS_KEY=<secret_key> -
Create a new s3 bucket by entering the following command:
$ aws s3 mb s3://<new_bucket_name> --region us-east-2Example output:
$ make_bucket: quay -
Upload all blobs to the new s3 bucket by entering the following command:
$ aws s3 sync --no-verify-ssl \ --endpoint-url <example_endpoint_url> (1) /tmp/quay-backup/blob-backup/. s3://quay/-
The Project Quay registry endpoint must be the same before backup and after restore.
Example output:
upload: ../../tmp/quay-backup/blob-backup/datastorage/registry/sha256/50/505edb46ea5d32b5cbe275eb766d960842a52ee77ac225e4dc8abb12f409a30d to s3://quay/datastorage/registry/sha256/50/505edb46ea5d32b5cbe275eb766d960842a52ee77ac225e4dc8abb12f409a30d upload: ../../tmp/quay-backup/blob-backup/datastorage/registry/sha256/27/27930dc06c2ee27ac6f543ba0e93640dd21eea458eac47355e8e5989dea087d0 to s3://quay/datastorage/registry/sha256/27/27930dc06c2ee27ac6f543ba0e93640dd21eea458eac47355e8e5989dea087d0 upload: ../../tmp/quay-backup/blob-backup/datastorage/registry/sha256/8c/8c7daf5e20eee45ffe4b36761c4bb6729fb3ee60d4f588f712989939323110ec to s3://quay/datastorage/registry/sha256/8c/8c7daf5e20eee45ffe4b36761c4bb6729fb3ee60d4f588f712989939323110ec ...
-
-
Before restarting your Project Quay deployment, update the storage settings in your config.yaml:
DISTRIBUTED_STORAGE_CONFIG: default: DISTRIBUTED_STORAGE_CONFIG: default: - S3Storage - s3_bucket: <new_bucket_name> storage_path: /registry s3_access_key: <s3_access_key> s3_secret_key: <s3_secret_key> s3_region: <region> host: <host_name>
Migrating a standalone Project Quay deployment to a Project Quay Operator deployment
The following procedures allow you to back up a standalone Project Quay deployment and migrate it to the Project Quay Operator on OpenShift Container Platform.
Backing up a standalone deployment of Project Quay
-
Back up the
config.yamlof your standalone Project Quay deployment:$ mkdir /tmp/quay-backup $ cp /path/to/Quay/config/directory/config.yaml /tmp/quay-backup -
Create a backup of the database that your standalone Project Quay deployment is using:
$ pg_dump -h DB_HOST -p 5432 -d QUAY_DATABASE_NAME -U QUAY_DATABASE_USER -W -O > /tmp/quay-backup/quay-database-backup.sql -
Install the AWS CLI if you do not have it already.
-
Create an
~/.aws/directory:$ mkdir ~/.aws/ -
Obtain the
access_keyandsecret_keyfrom theconfig.yamlof your standalone deployment:$ grep -i DISTRIBUTED_STORAGE_CONFIG -A10 /tmp/quay-backup/config.yamlExample output:
DISTRIBUTED_STORAGE_CONFIG: minio-1: - RadosGWStorage - access_key: ########## bucket_name: quay hostname: 172.24.10.50 is_secure: false port: "9000" secret_key: ########## storage_path: /datastorage/registry -
Store the
access_keyandsecret_keyfrom theconfig.yamlfile in your~/.awsdirectory:$ touch ~/.aws/credentials -
Optional: Check that your
access_keyandsecret_keyare stored:$ cat > ~/.aws/credentials << EOF [default] aws_access_key_id = ACCESS_KEY_FROM_QUAY_CONFIG aws_secret_access_key = SECRET_KEY_FROM_QUAY_CONFIG EOFExample output:
aws_access_key_id = ACCESS_KEY_FROM_QUAY_CONFIG aws_secret_access_key = SECRET_KEY_FROM_QUAY_CONFIGNoteIf the
aws clidoes not automatically collect theaccess_keyandsecret_keyfrom the`~/.aws/credentials file, you can, you can configure these by runningaws configureand manually inputting the credentials. -
In your
quay-backupdirectory, create abucket_backupdirectory:$ mkdir /tmp/quay-backup/bucket-backup -
Backup all blobs from the S3 storage:
$ aws s3 sync --no-verify-ssl --endpoint-url https://PUBLIC_S3_ENDPOINT:PORT s3://QUAY_BUCKET/ /tmp/quay-backup/bucket-backup/NoteThe
PUBLIC_S3_ENDPOINTcan be read from the Project Quayconfig.yamlfile underhostnamein theDISTRIBUTED_STORAGE_CONFIG. If the endpoint is insecure, usehttpinstead ofhttpsin the endpoint URL.
Up to this point, you should have a complete backup of all Project Quay data, blobs, the database, and the config.yaml file stored locally. In the following section, you will migrate the standalone deployment backup to Project Quay on OpenShift Container Platform.
Using backed up standalone content to migrate to OpenShift Container Platform.
-
Your standalone Project Quay data, blobs, database, and
config.yamlhave been backed up. -
Project Quay is deployed on OpenShift Container Platform using the Project Quay Operator.
-
A
QuayRegistrywith all components set tomanaged.
|
Note
|
Procedure
The procedure in this documents uses the following namespace: |
-
Scale down the Project Quay Operator:
$ oc scale --replicas=0 deployment quay-operator.v3.6.2 -n openshift-operators -
Scale down the application and mirror deployments:
$ oc scale --replicas=0 deployment QUAY_MAIN_APP_DEPLOYMENT QUAY_MIRROR_DEPLOYMENT -
Copy the database SQL backup to the
QuayPostgreSQL database instance:$ oc cp /tmp/user/quay-backup/quay-database-backup.sql quay-enterprise/quayregistry-quay-database-54956cdd54-p7b2w:/var/lib/pgsql/data/userdata -
Obtain the database password from the Operator-created
config.yamlfile:$ oc get deployment quay-quay-app -o json | jq '.spec.template.spec.volumes[].projected.sources' | grep -i config-secretExample output:
"name": "QUAY_CONFIG_SECRET_NAME"$ oc get secret quay-quay-config-secret-9t77hb84tb -o json | jq '.data."config.yaml"' | cut -d '"' -f2 | base64 -d -w0 > /tmp/quay-backup/operator-quay-config-yaml-backup.yamlcat /tmp/quay-backup/operator-quay-config-yaml-backup.yaml | grep -i DB_URIExample output:
postgresql://QUAY_DATABASE_OWNER:PASSWORD@DATABASE_HOST/QUAY_DATABASE_NAME
-
Execute a shell inside of the database pod:
# oc exec -it quay-postgresql-database-pod -- /bin/bash -
Enter psql:
bash-4.4$ psql -
Drop the database:
postgres=# DROP DATABASE "example-restore-registry-quay-database";Example output:
DROP DATABASE
-
Create a new database and set the owner as the same name:
postgres=# CREATE DATABASE "example-restore-registry-quay-database" OWNER "example-restore-registry-quay-database";Example output:
CREATE DATABASE
-
Connect to the database:
postgres=# \c "example-restore-registry-quay-database";Example output:
You are now connected to database "example-restore-registry-quay-database" as user "postgres". -
Create a
pg_trmgextension of yourQuaydatabase:example-restore-registry-quay-database=# create extension pg_trgm ;Example output:
CREATE EXTENSION -
Exit the postgres CLI to re-enter bash-4.4:
\q -
Set the password for your PostgreSQL deployment:
bash-4.4$ psql -h localhost -d "QUAY_DATABASE_NAME" -U QUAY_DATABASE_OWNER -W < /var/lib/pgsql/data/userdata/quay-database-backup.sqlExample output:
SET SET SET SET SET
-
Exit bash mode:
bash-4.4$ exit -
Create a new configuration bundle for the Project Quay Operator.
$ touch config-bundle.yaml -
In your new
config-bundle.yaml, include all of the information that the registry requires, such as LDAP configuration, keys, and other modifications that your old registry had. Run the following command to move thesecret_keyto yourconfig-bundle.yaml:$ cat /tmp/quay-backup/config.yaml | grep SECRET_KEY > /tmp/quay-backup/config-bundle.yamlNoteYou must manually copy all the LDAP, OIDC and other information and add it to the /tmp/quay-backup/config-bundle.yaml file.
-
Create a configuration bundle secret inside of your OpenShift cluster:
$ oc create secret generic new-custom-config-bundle --from-file=config.yaml=/tmp/quay-backup/config-bundle.yaml -
Scale up the
Quaypods:$ oc scale --replicas=1 deployment quayregistry-quay-app deployment.apps/quayregistry-quay-app scaled
-
Scale up the mirror pods:
$ oc scale --replicas=1 deployment quayregistry-quay-mirror deployment.apps/quayregistry-quay-mirror scaled
-
Patch the
QuayRegistryCRD so that it contains the reference to the new custom configuration bundle:$ oc patch quayregistry QUAY_REGISTRY_NAME --type=merge -p '{"spec":{"configBundleSecret":"new-custom-config-bundle"}}'NoteIf Project Quay returns a
500internal server error, you might have to update thelocationof yourDISTRIBUTED_STORAGE_CONFIGtodefault. -
Create a new AWS
credentials.yamlin your/.aws/directory and include theaccess_keyandsecret_keyfrom the Operator-createdconfig.yamlfile:$ touch credentials.yaml$ grep -i DISTRIBUTED_STORAGE_CONFIG -A10 /tmp/quay-backup/operator-quay-config-yaml-backup.yaml$ cat > ~/.aws/credentials << EOF [default] aws_access_key_id = ACCESS_KEY_FROM_QUAY_CONFIG aws_secret_access_key = SECRET_KEY_FROM_QUAY_CONFIG EOFNoteIf the
aws clidoes not automatically collect theaccess_keyandsecret_keyfrom the`~/.aws/credentials file, you can configure these by runningaws configureand manually inputting the credentials. -
Record the NooBaa’s publicly available endpoint:
$ oc get route s3 -n openshift-storage -o yaml -o jsonpath="{.spec.host}{'\n'}" -
Sync the backup data to the NooBaa backend storage:
$ aws s3 sync --no-verify-ssl --endpoint-url https://NOOBAA_PUBLIC_S3_ROUTE /tmp/quay-backup/bucket-backup/* s3://QUAY_DATASTORE_BUCKET_NAME -
Scale the Operator back up to 1 pod:
$ oc scale –replicas=1 deployment quay-operator.v3.6.4 -n openshift-operators
The Operator uses the custom configuration bundle provided and reconciles all secrets and deployments. Your new Project Quay deployment on OpenShift Container Platform should contain all of the information that the old deployment had. You should be able to pull all images.
Project Quay garbage collection
Project Quay includes automatic and continuous image garbage collection. Garbage collection ensures efficient use of resources for active objects by removing objects that occupy sizeable amounts of disk space, such as dangling or untagged images, repositories, and blobs, including layers and manifests. Garbage collection performed by Project Quay can reduce downtime in your organization’s environment.
Project Quay garbage collection in practice
Currently, all garbage collection happens discreetly, and there are no commands to manually run garbage collection. Project Quay provides metrics that track the status of the different garbage collection workers.
For namespace and repository garbage collection, the progress is tracked based on the size of their respective queues. Namespace and repository garbage collection workers require a global lock to work. As a result, and for performance reasons, only one worker runs at a time.
|
Note
|
Project Quay shares blobs between namespaces and repositories in order to conserve disk space. For example, if the same image is pushed 10 times, only one copy of that image will be stored. It is possible that tags can share their layers with different images already stored somewhere in Project Quay. In that case, blobs will stay in storage, because deleting shared blobs would make other images unusable. Blob expiration is independent of the time machine. If you push a tag to Project Quay and the time machine is set to 0 seconds, and then you delete a tag immediately, garbage collection deletes the tag and everything related to that tag, but will not delete the blob storage until the blob expiration time is reached. |
Garbage collecting tagged images works differently than garbage collection on namespaces or repositories. Rather than having a queue of items to work with, the garbage collection workers for tagged images actively search for a repository with inactive or expired tags to clean up. Each instance of garbage collection workers will grab a repository lock, which results in one worker per repository.
|
Note
|
|
For each type of garbage collection, Project Quay provides metrics for the number of rows per table deleted by each garbage collection worker. The following image shows an example of how Project Quay monitors garbage collection with the same metrics:
Measuring storage reclamation
Project Quay does not have a way to track how much space is freed up by garbage collection. Currently, the best indicator of this is by checking how many blobs have been deleted in the provided metrics.
|
Note
|
The |
Garbage collection configuration fields
The following configuration fields are available to customize what is garbage collected, and the frequency at which garbage collection occurs:
| Name | Description | Schema |
|---|---|---|
FEATURE_GARBAGE_COLLECTION |
Whether garbage collection is enabled for image tags. Defaults to |
Boolean |
FEATURE_NAMESPACE_GARBAGE_COLLECTION |
Whether garbage collection is enabled for namespaces. Defaults to |
Boolean |
FEATURE_REPOSITORY_GARBAGE_COLLECTION |
Whether garbage collection is enabled for repositories. Defaults to |
Boolean |
GARBAGE_COLLECTION_FREQUENCY |
The frequency, in seconds, at which the garbage collection worker runs. Affects only garbage collection workers. Defaults to 30 seconds. |
String |
PUSH_TEMP_TAG_EXPIRATION_SEC |
The number of seconds that blobs will not be garbage collected after being uploaded. This feature prevents garbage collection from cleaning up blobs that are not referenced yet, but still used as part of an ongoing push. |
String |
TAG_EXPIRATION_OPTIONS |
List of valid tag expiration values. |
String |
DEFAULT_TAG_EXPIRATION |
Tag expiration time for time machine. |
String |
CLEAN_BLOB_UPLOAD_FOLDER |
Automatically cleans stale blobs left over from an S3 multipart upload. By default, blob files older than two days are cleaned up every hour. |
Boolean +
Default: |
Disabling garbage collection
The garbage collection features for image tags, namespaces, and repositories are stored in the config.yaml file. These features default to True.
In rare cases, you might want to disable garbage collection, for example, to control when garbage collection is performed. You can disable garbage collection by setting the GARBAGE_COLLECTION features to False. When disabled, dangling or untagged images, repositories, namespaces, layers, and manifests are not removed. This might increase the downtime of your environment.
|
Note
|
There is no command to manually run garbage collection. Instead, you would disable, and then re-enable, the garbage collection feature. |
Garbage collection and quota management
Project Quay introduced quota management in 3.7. With quota management, users have the ability to report storage consumption and to contain registry growth by establishing configured storage quota limits.
As of Project Quay 3.7, garbage collection reclaims memory that was allocated to images, repositories, and blobs after deletion. Because the garbage collection feature reclaims memory after deletion, there is a discrepancy between what is stored in an environment’s disk space and what quota management is reporting as the total consumption. There is currently no workaround for this issue.
Garbage collection in practice
Use the following procedure to check your Project Quay logs to ensure that garbage collection is working.
-
Enter the following command to ensure that garbage collection is properly working:
$ sudo podman logs <container_id>Example output:
gcworker stdout | 2022-11-14 18:46:52,458 [63] [INFO] [apscheduler.executors.default] Job "GarbageCollectionWorker._garbage_collection_repos (trigger: interval[0:00:30], next run at: 2022-11-14 18:47:22 UTC)" executed successfully -
Delete an image tag.
-
Enter the following command to ensure that the tag was deleted:
$ podman logs quay-appExample output:
gunicorn-web stdout | 2022-11-14 19:23:44,574 [233] [INFO] [gunicorn.access] 192.168.0.38 - - [14/Nov/2022:19:23:44 +0000] "DELETE /api/v1/repository/quayadmin/busybox/tag/test HTTP/1.0" 204 0 "http://quay-server.example.com/repository/quayadmin/busybox?tab=tags" "Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0"
Project Quay garbage collection metrics
The following metrics show how many resources have been removed by garbage collection. These metrics show how many times the garbage collection workers have run and how many namespaces, repositories, and blobs were removed.
| Metric name | Description |
|---|---|
quay_gc_iterations_total |
Number of iterations by the GCWorker |
quay_gc_namespaces_purged_total |
Number of namespaces purged by the NamespaceGCWorker |
quay_gc_repos_purged_total |
Number of repositories purged by the RepositoryGCWorker or NamespaceGCWorker |
quay_gc_storage_blobs_deleted_total |
Number of storage blobs deleted |
# TYPE quay_gc_iterations_created gauge
quay_gc_iterations_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.6317823190189714e+09
...
# HELP quay_gc_iterations_total number of iterations by the GCWorker
# TYPE quay_gc_iterations_total counter
quay_gc_iterations_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
...
# TYPE quay_gc_namespaces_purged_created gauge
quay_gc_namespaces_purged_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.6317823190189433e+09
...
# HELP quay_gc_namespaces_purged_total number of namespaces purged by the NamespaceGCWorker
# TYPE quay_gc_namespaces_purged_total counter
quay_gc_namespaces_purged_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
....
# TYPE quay_gc_repos_purged_created gauge
quay_gc_repos_purged_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.631782319018925e+09
...
# HELP quay_gc_repos_purged_total number of repositories purged by the RepositoryGCWorker or NamespaceGCWorker
# TYPE quay_gc_repos_purged_total counter
quay_gc_repos_purged_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
...
# TYPE quay_gc_storage_blobs_deleted_created gauge
quay_gc_storage_blobs_deleted_created{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 1.6317823190189059e+09
...
# HELP quay_gc_storage_blobs_deleted_total number of storage blobs deleted
# TYPE quay_gc_storage_blobs_deleted_total counter
quay_gc_storage_blobs_deleted_total{host="example-registry-quay-app-6df87f7b66-9tfn6",instance="",job="quay",pid="208",process_name="secscan:application"} 0
...Performing health checks on Project Quay deployments
To monitor the health of your {product-title} deployment and identify issues before they become critical, you can perform health checks. Health checks assess system functionality and provide information about the current state for troubleshooting.
Health checks help ensure that everything is working correctly, and can be used to identify potential issues before they become critical problems. By monitoring the health of a system, Project Quay administrators can address abnormalities or potential failures for things like geo-replication deployments, Operator deployments, standalone Project Quay deployments, object storage issues, and so on. Performing health checks can also help reduce the likelihood of encountering troubleshooting scenarios. Health check mechanisms can play a role in diagnosing issues by providing valuable information about the system’s current state. By comparing health check results with expected benchmarks or predefined thresholds, deviations or anomalies can be identified quicker.
|
Important
|
Links contained herein to any external website(s) are provided for convenience only. Red Hat has not reviewed the links and is not responsible for the content or its availability. The inclusion of any link to an external website does not imply endorsement by Red Hat of the website or its entities, products, or services. You agree that Red Hat is not responsible or liable for any loss or expenses that may result due to your use of (or reliance on) the external site or content. |
Project Quay has several health check endpoints. The following table shows you the health check, a description, an endpoint, and an example output.
| Health check | Description | Endpoint | Example output |
|---|---|---|---|
|
The |
|
|
|
The |
|
|
|
The |
|
Branding a Project Quay deployment on the legacy UI
You can brand the UI of your Project Quay deployment by changing the registry title, logo, footer image, and by directing users to a website embedded in the footer image.
-
Update your Project Quay
config.yamlfile to add the following parameters:BRANDING: logo: (1) footer_img: (2) footer_url: (3) --- REGISTRY_TITLE: (4) REGISTRY_TITLE_SHORT: (5)-
The URL of the image that will appear at the top of your Project Quay deployment.
-
The URL of the image that will appear at the bottom of your Project Quay deployment.
-
The URL of the website that users will be directed to when clicking the footer image.
-
The long-form title for the registry. This is displayed in frontend of your Project Quay deployment, for example, at the sign in page of your organization.
-
The short-form title for the registry. The title is displayed on various pages of your organization, for example, as the title of the tutorial on your organization’s Tutorial page.
-
-
Restart your Project Quay deployment. After restarting, your Project Quay deployment is updated with a new logo, footer image, and footer image URL.
Preparing your registry to accept large artifacts
|
Important
|
Before altering the Altering this field can also slow down uploads. You should only alter this field if necessary. |
Artificial intelligent (AI) or machine learning (ML) artifacts such as large-language models (LLMs), vector graphics, trained model files, or large datasets often require that Project Quay administrators modify their registry to suit the needs of pushing such larger artifacts. By default, Project Quay is configured with a minimum chunk size (or the pieces that a large file is split into during upload) of 5 MB. This means that larger layers, for example, 50 GB, result in 10,000 chunks. This can be confirmed based on the following formula:
-
50 GB = 50,000 MB
-
50,000 MB divided by Project Quay’s default minimum chunk size of 5 MB = 10,000 chunks
Some backend storage providers, for example, Amazon Web Services (AWS) S3, are unable to store artifacts larger than 50 GB because of a strict limitation of 10,000 parts per upload; attempting to push an artifact larger than 50 GB with Project Quay’s default of 5 MB results in S3 protocol violations.
As a workaround to this limitation, you can set the minimum_chunk_size_mb field in your config.yaml file to a value larger than 5 MB. For example:
# ...
minimum_chunk_size_mb: 20
# ...Configuring minimum_chunk_size_mb to more than 5 MB allows your registry backend to accept artifacts larger than 50 GB and up to 200 GB. In the event that your artifact is larger than 200 GB, you could increase the minimum_chunk_size_mb value.
Consult with Red Support before altering the minimum_chunk_size_mb configuration field.
Schema for Project Quay configuration
Most Project Quay configuration information is stored in the config.yaml file. All configuration options are described in the Project Quay Configuration Guide.